In the following section, you learn about ways to
secure data in storage and how to configure security templates to deploy
to one or many computers. These topics include
Windows Security Center
BitLocker
The Encrypting File System (EFS)
Security Configuration and Analysis Tool (SCAT)
The SecEdit command-line utility
The Windows Security Center
The Windows Security Center
is installed by default in Windows Vista. It integrates, monitors, and
alerts problems for the following security-related tools:
You can access the
Security Center in the Control Panel > Security > Security Center
or by double-clicking the yellow or red shield in the system tray.
Tip
The yellow or red shield in the
system tray is presented only if the Security Center detects a problem
with one or more of the security components that it monitors. A yellow
shield in the system tray indicates a security warning, and a red shield
indicates a critical security problem.
In the Security Center,
you can view the security status of each of these security services and
gain quick access to each of the tools to make any desired configuration
changes. You can configure the level of alerts and whether the Security
Center places an icon in the system tray in the right corner of the
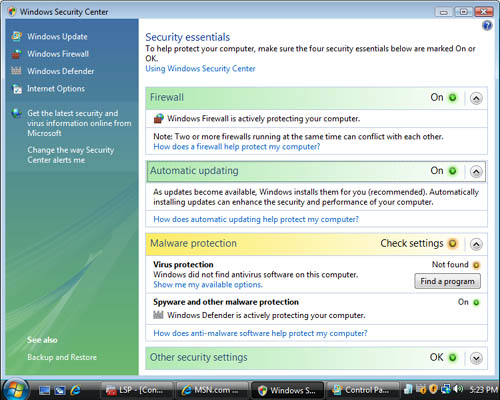
taskbar. As you can see in Figure 1,
the shield icon in the system tray is a warning, and it’s alerting you
to the fact that the Security Center cannot identify an antivirus
application running on your computer.
Alert
This
warning can be eliminated if you simply install an antivirus software
product that is Windows Vista compliant. Antivirus software for earlier
versions of Windows is not necessarily compliant with Windows Vista. The
antivirus software packaging must specifically say that it is Windows
Vista compliant.
The
way these third-party antivirus products properly report to the
Security Center is through a Microsoft Windows Management
Instrumentation (WMI) interface. If the antivirus software uses the WMI
interface, the Windows Security Center can monitor it and should change
the yellow shield warning indication to a green shield indicating a
healthy, protected computer system.
Another option you have to
eliminate the yellow shield warning from the Windows Security Center is
to install and subscribe to a new subscription product from Microsoft
called Windows Live OneCare, as shown in Figure 2.
Tip
The Windows Security Center also provides quick access to the Backup and Restore Center.
Securing the Operating System and Data in Storage with BitLocker
BitLocker
is an encrypting technology that has been introduced in Windows Vista.
It is included with Windows Vista Ultimate and with Windows Vista
Enterprise. BitLocker encrypts the entire volume (partition) that holds
the operating system. This is referred to as the boot partition.
BitLocker is designed to protect against a bad guy who could take the
hard drive out of your computer, install it into his computer, and
access all your content. After BitLocker is installed, the operating
system and file system cannot be accessed without the decryption key.
Caution
Use Caution with BitLocker
BitLocker is powerful security but may also cause you to lose valuable
data. It requires a specialized partition structure and a lengthy
process to encrypt the entire boot partition. Repartitioning and
encrypting the partition are both opportunities for total data loss.
Also, if you lose the decryption key, you could never see your OS or
data again. Even when it works correctly, the system is now operating
like it never did before.
Consider implementing
BitLocker carefully. Read all the documentation on BitLocker from
Microsoft. Then back up all your data, drivers, and so on, from the
computer as if you know that you’re going to lose it all. And most
importantly, know how to recover your content if necessary, from your
backup and from BitLocker, before you ever begin the BitLocker process.
The decryption key for
the BitLocker partition is held in a special chip on the motherboard
called the Trusted Platform Module (TPM) chip. Not all motherboards have
this TPM chip; in fact, most computers today don’t have one because the
technology is relatively new.
If your computer doesn’t
have a TPM chip, you can export the decryption key to a Universal Serial
Bus (USB) thumb drive. This makes the USB thumb drive a sort of
SmartCard. Without the USB thumb drive with the decryption key inserted
into a USB port during the bootup process, the entire boot partition
remains encrypted and inaccessible. This is strong security.
This security is a good
thing and a bad thing. If the TPM chip fails (I don’t really think that
these chips have a high failure rate, but just in case) or if you lose
your USB thumb drive that holds the decryption key (something more
likely to happen), you simply cannot access your computer’s Vista
operating system and whatever data the partition held ever again.
Alert
When
you implement BitLocker, you should generate a recovery password and
store it on something other than the computer you are protecting.
Storing this password on the same computer would defeat the purpose of
using BitLocker. You should store the recovery password on a USB thumb
drive in an ASCII text file. (This is a different USB thumb drive from
the BitLocker bootup USB thumb drive.) This drive with the BitLocker
recovery password should be stored securely someplace where only you can
find it when you need it.
After
you have generated and recorded the BitLocker Recovery Password, if the
TPM chip ever fails, or if you lose your BitLocker bootup USB thumb
drive, you can open the text file, retrieve your BitLocker recovery
password, and boot into the BitLocker Drive Encryption Recovery Console
to access the encrypted operating system. Once there, you can generate a
new BitLocker bootup USB thumb drive, export data, or do whatever else
you need to do to regain access to your system.