Microsoft’s Windows Defender
is a free tool that gets installed automatically with Windows Vista. It
finds and tries to remove malicious software and other unwanted
programs, often called malware or spyware.
This malware can slow down your computer, display annoying pop-up ads,
change Internet settings, or use your private information without your
consent.
Alert
Windows Defender scans you computer for malware within programs on a schedule (called a Scan) and can scan program files when you launch applications (called real-time protection).
It quarantines known spyware and executables that exhibit undesirable
behavior. Windows Defender tries to remove or quarantine these bad
applications without negatively affecting your data and without losing
any of your installed applications.
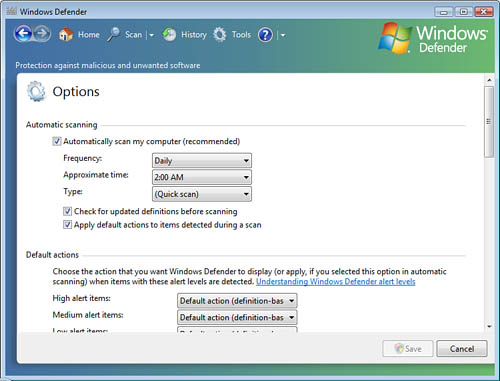
You can configure Windows
Defender to handle different levels of threatening behavior differently,
on the Tools > Options dialog box, as shown in Figure 1.
Windows Defender ranks the threat levels of malware as Low, Medium,
High, Severe, and Not Yet Classified. By default, Windows Defender
immediately quarantines Severe and High threat level programs. You can
configure the way Windows Defender reacts when it detects malicious
software.
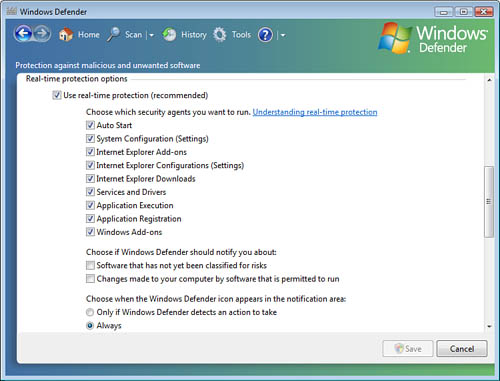
By
scrolling down in this same dialog box, you can configure the way that
Windows Defender alerts you when it finds malware, as shown in Figure 2.
Because Windows
Defender automatically quarantines applications that meet its definition
of “threatening,” it may quarantine an application that you know to be
safe and desirable. While the application is quarantined, you cannot
launch the application. If Windows Defender quarantines a program that
you choose to run, you can easily restore the program to its normal
state in the Tools > Quarantined Items dialog box.
Caution
Removing Applications from Windows Defender’s Quarantine
Just because you want to use an application does not mean that the
application is safe to be used. Applications can be placed in quarantine
because they are known to be malicious, because they appear to be
infected, or because they exhibit risky behavior. Removing an
application from the Windows Defender quarantine could be a dangerous
decision that can severely affect the security of your computer. Don’t
do this unless you truly know that the application is safe, or unless
you are willing to accept the risk of having your computer being
exploited by the bad guys and having your private information exposed.
Windows Defender’s Logging Capabilities
Windows
Defender also monitors all the programs that are running, looking for
potentially harmful or unwanted behavior by the running processes. This
is called real-time protection.
As a byproduct of monitoring all running applications, you can enable
logging of all known good applications and all unknown applications that
are running on the computer. This increased logging can be configured
in the Local Computer Policy on one computer or by Group Policy Objects (GPOs) if you are in an Active Directory environment.
Microsoft’s SpyNet Program
Windows Defender’s
default settings provide automatic updating of the malware signature
database. Windows Defender also reports back to Microsoft on the
software that it has seen and taken action on through its SpyNet
program. This is an optional service that you can choose whether to
participate in. The SpyNet program collects malware statistics from
Windows Defender on computers in an attempt to keep Microsoft’s malware
signature database current. SpyNet is designed to collect a minimum of
personal information and takes steps to ensure your anonymity.
You can opt out of the Microsoft SpyNet program by going to the History page in Windows Defender’s Options and selecting the Change Settings
hyperlink adjacent to the SpyNet reference. You can view the items that
you have chosen to have Windows Defender allow, as well as the items
that Windows Defender has quarantined. These last two items can also be
accessed from the Options page.
Alert
Another
cool tool in Windows Defender is the Software Explorer, which is also
accessed from the Tools dialog box. This tool shows you detailed
information about all the programs running on your computer, as shown in
Figure 3.
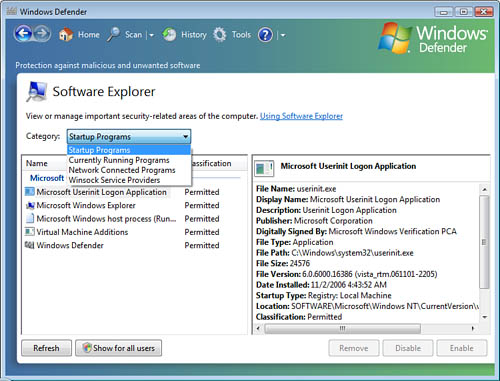
The Software Explorer tool inside Windows Defender can display the running applications by grouping them into four categories:
Startup Programs— Programs that launch at startup
Currently Running Programs— Everything running on the desktop and in the background
Network-Connected Programs— Programs that are connected to other computers over the network or the Internet
Winsock Service Providers— Programs that assist network-connected programs
Windows Defender relies on an underlying service called (surprise!) Windows Defender, as shown in Figure 4.
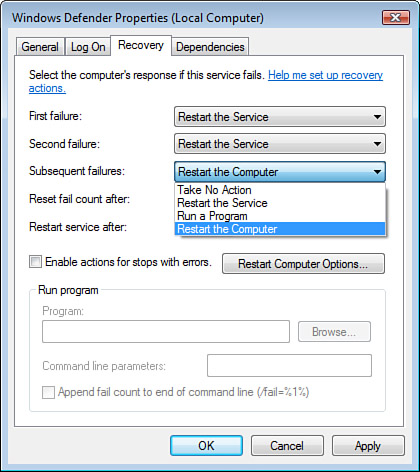
To
ensure that this service stays running keeping your malware protection
in force, you might want to configure the Windows Defender service to
restart automatically if it ever gets shut down. You can configure the
service to restart on the first and second failure of the service. If
the service doesn’t remain started, you can configure the service to try
for what is called Trusted Recovery. On the third shutdown of the service, reboot the computer.
Caution
Using Service Recovery This service recovery configuration can be utilized on any service that runs on a Microsoft-based computer.
Be aware that
restarting a computer automatically, as previously described, can cause
serious problems and, potentially, the loss of data. This should be
implemented on computers only after careful consideration of the
ramifications of forcing an automatic shutdown and restart of the
system.
MSConfig.exe
Another useful tool in
the battle to protect your computer from bad things is called the System
Configuration Utility, or MSConfig. You can launch MSConfig.exe, shown in Figure 5, from the Start > Run (or the Start > Search) command line. Just type msconfig and click Enter.
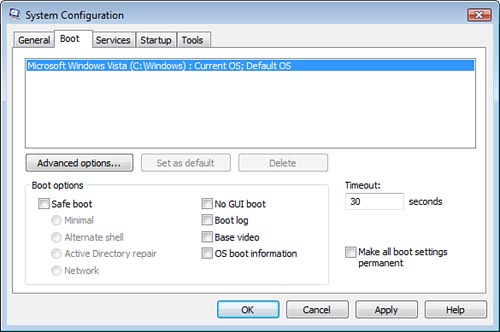
You can use MSConfig to
configure Normal, Diagnostic, or Selective startup on the General tab;
adjust the Startup menu (instead of using BCDEdit) on the Boot tab;
enable or disable services on the Services tab; view all programs that
are configured to run at computer startup or at user logon on the
Startup tab; or launch a number of configuration and diagnostic tools
from the Tools tab.
Caution
Configuration Changes with MSConfig.exe
Making changes to the startup configuration of the computer can cause
applications and services to fail, or even cause the system to fail to
boot up successfully. Don’t make any changes to the startup
configuration unless you understand what the results will be and know
how to recover if the results you get are unexpected.
The hosts File
One bad thing that
malware might do is try to keep you disconnected from websites that help
you identify malware, like the Windows Update and the antivirus
definitions update websites. Malware often tries to block your access to
these websites by adding incorrect mappings into the hosts file on your computer.
Note
A Word About the hosts File The hosts file can be edited with Notepad.exe and is located in the \Windows\System32\Drivers\etc folder. The hosts file is used to map computer hostnames (like webserver1) and fully qualified domain names (FQDNs, like www.microsoft.com) to their IP address.
If malware modifies your hosts file, your computer thinks it knows where to find these helpful websites by looking in the hosts
file. Your computer never asks public DNS servers where to find the
actual websites. Because malware has incorrectly mapped these websites
to the loopback address of 127.0.0.1 or some other incorrect IP address,
your computer can never connect to the update sites and never gets the
new updates and security updates that might just find the original
malware.
Alert
If
you discover that your computer is not getting updates for the
operating system, applications, and not getting new definition files for
antivirus programs or anti-spyware programs, first try to kill the
malware by running a Windows Defender scan and an antivirus scan and
then enabling a pop-up blocker.
Then use Notepad.exe, as shown in Figure 6, to open the hosts file and delete any lines other than the localhost mappings. One localhost mapping is to the loopback IPv4 address of 127.0.0.1 and another localhost mapping to the IPv6 loopback address of ::1. When you save the hosts file, you should be able to get to these beneficial websites again.
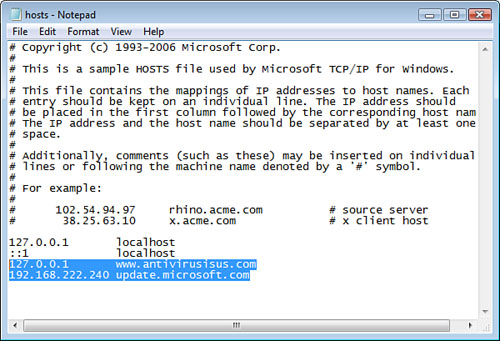
Getting Rid of Malware
While
you probably have installed antivirus software, and you use Windows
Defender to perform automatic removal of malware, sometimes you can
simply uninstall the malware. Malware, like an unwanted Internet
Explorer toolbar that installs with some third-party software update,
can often be uninstalled from the Control Panel > Programs and
Features section. Simply click Uninstall a Program. Then click on the program that you desire to remove and click Uninstall from the overhead menu.
Sometimes it isn’t that easy to get rid of malware, and a more rigorous approach is required.
RootkitRevealer
If you are really
concerned about undetected malware, Microsoft and Sysinternals have a
tool called RootkitRevealer. It is a specially designed utility to
detect rootkits and can be downloaded from the following website:
http://www.microsoft.com/technet/sysinternals/utilities/RootkitRevealer.mspx
Rootkits are what bad
guys upload to your computer when they pretty much have taken over. It
is a collection of malware tools and “trojaned” applications that are
designed to take control and keep control of an exploited system. The
bad guys have gotten good at hiding these malicious tools from antivirus
and anti-spyware detectors.
Caution
RootkitRevealer Is Buggy with Vista
At the time of this writing, this RootkitRevealer tool wasn’t exactly
Vista compatible. As a matter of fact, after I installed and ran
RootkitRevealer, I had to restore the Vista system I used it on from a
previous system restore point. But keep RootkitRevealer in mind for
malware protection on Vista systems in the future and for the exam. My
bet is that Microsoft will be releasing a new Vista-compatible version
of RootkitRevealer in the near future.