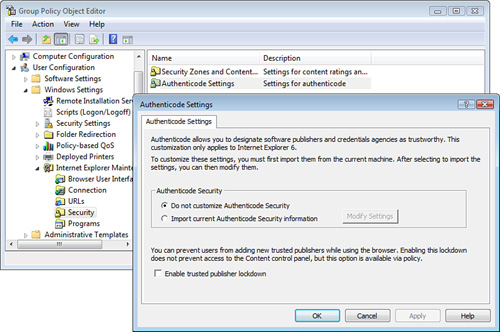
Point and Print
Restrictions
Point and Print restrictions allow you to control access to
selected shared printers on the corporate network. By default, printers
are shared with the permissions set to Allow—Print for the Everyone
group. This says that any user can connect to a shared printer,
automatically download any required printer drivers, and submit print
jobs to that device. Permissions can be adjusted on the printer
properties to further control this access. The Point and Print
restrictions in a GPO can be used in addition to these permissions to
control printer access for large groups of users in an AD environment.
This setting is located
under User Configuration > Administrative Templates > Control
Panel > Printers, as shown in Figure 11.
The fully
qualified domain name (FQDN) of the
print server must be added to complete the GPO setting.
This GPO setting requires that
you construct a list of print servers that the users are allowed to
download drivers from and then submit print jobs to. You can further
restrict the driver download to only those drivers that have been
tested, approved, and digitally signed by Microsoft’s Windows Hardware
Quality Labs (WHQL), the testing arm of Microsoft for third-party
drivers.
Digital Certificates
and Authenticode
As users connect to web servers, their
browsers download the HTML file and image files and also download and
execute active content, like ActiveX controls. Active content, also
called mobile code,
is a major source of malware (viruses and spyware) and is often heavily
restricted in a corporate environment.
To ensure that your
ActiveX controls are safe and usable by all who visit your website is to
have the ActiveX control tested and digitally signed by Microsoft. When
an ActiveX control is signed by Microsoft, it is called Authenticode, and it
is generally trusted to be safe for your users to run. However, on
occasion, these tested and approved ActiveX controls can still conflict
with other software running on your client computers, so having it
signed by Microsoft is still not a guarantee of safety.
Caution
Be
Careful with Authenticode Restrictions
Enabling restrictions on your browsers to allow only approved
publishers of Authenticode enhances the security of browsing but can
cause web applications and other website functions that rely on unsigned
and unapproved publishers of ActiveX controls to fail.
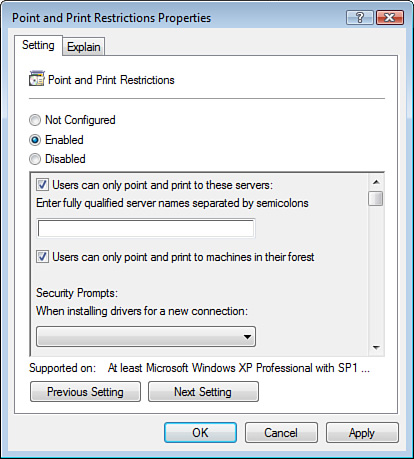
You can restrict the
browsers on your users’ computers to execute Authenticode only from a
select list of publishers that you approve. To do this, you must enable a
setting in a GPO that is located under User Configuration > Windows
Settings > Internet Explorer Maintenance > Security >
Authenticode Settings. The setting is labeled Enable Trusted Publisher
Lockdown. This setting, shown in Figure 12, disables users from accepting any certificates (used
in the Authenticode) from publishers that aren’t on your approved
publishers list.