The Audit Policy
Auditing is a
critical component of the security program for every company. You can
configure systems to record what your users do (Success) and what your
users attempt to do (Failure). Audit policies are defined within the
Local Computer Policy (LCP) and within GPOs. The audit policy is located
under Computer Configuration > Windows Settings > Security
Settings > Local Policies > Audit Policy. You can configure nine
audit policies, as shown in Figure 9.
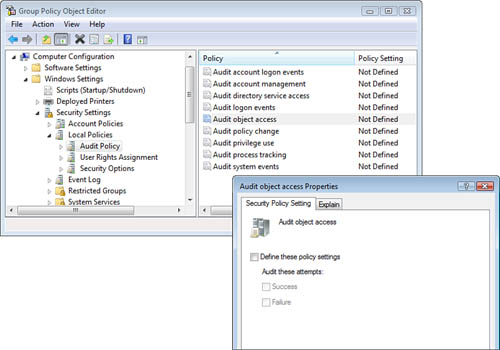
Audited events get recorded in
the Security log on the computer where the event occurs and can be
reviewed in the Event Viewer on that computer. The Security logs (and
any other types of events) from multiple Windows Vista computers can be
forwarded to an Event Collector server.
Most of the audit
policies require only the LCP or GPO settings configured to be
effective. Two of the audit policies require some additional
configuration in addition to the GPO audit policy settings to be
effective. They are Directory Service Access and Object Access policies.
The additional settings that are required reside on the properties of
the objects being tracked by the audit policy and must be configured on
the objects’ System Access Control List (SACL). (This may also be called
the Security Access Control List—SACL.) The GPO turns on the auditing
engine, and the SACL identifies specifically which users and which
objects will be tracked.
You can access the SACL by following these steps:
1. | Right-click
on the Files, Folders, Printers,
or AD objects of interest and select
Properties.
|
2. | Select
the Security tab and click Advanced.
|
3. | Select the Auditing
tab to access the SACL for these types of objects.
|
Tip
If
the Security tab is not visible on AD objects, you must select View > Advanced Features from the menu
to enable it.
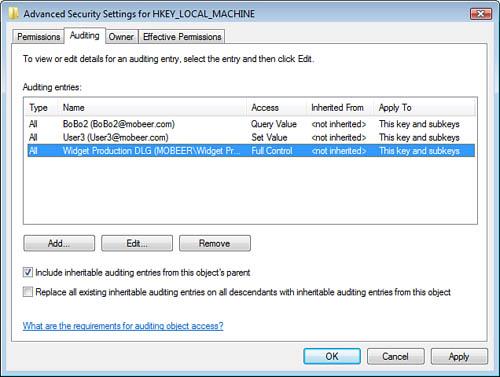
On Registry objects,
after enabling the Audit Object Access audit policy, right-click the
desired Registry object and select Permissions.
Click Advanced and select the Auditing tab. This
is the SACL for Registry Keys, Values, and Data, as shown in Figure 10.
Alert
The
following is a review of what each audit policy setting accomplishes:
Audit Account Logon Events— Logs a user’s domain
account logons on the domain controller (DC).
Audit Account Management—
Logs changes to
user objects in AD.
Audit Directory Service Access— Logs access to objects in AD.
This audit policy setting requires the additional SACL configuration on
the AD objects of interest.
Audit Logon Events— Logs a user’s local
account logons on the local computer.
Audit Object Access— Logs access to Files,
Folders, Printers, and Registry components (Keys, Values, and Data).
This audit policy setting requires the additional SACL configuration on
the objects of interest.
Audit Policy Change— Logs changes to user
rights, auditing, or trust settings within GPOs.
Audit Privilege Use— Logs the use of rights
that have been granted.
Audit Process Tracking— Logs actions of
and interactions between applications.
Audit System Events— Logs shutdowns and events
that affect the System or Security logs.
Understand
the difference between the Audit Account Logon Events and the Audit
Logon Events audit policies!