4. Determining When Your System Is Infected with Malware
As a enterprise support technician, you need to know how to recognize the symptoms of a
malware infection on your client computers. Then, if your antivirus and anti-spyware are
not functioning or not detecting any malware, you need to know how to remove malware
manually.
Here are a few common signs of a computer being infected by a virus, worm, or Trojan
horse:
Sluggish computer performance
Unusual error messages
Distorted menus and dialog boxes
Antivirus software repeatedly turning itself off
Screen freezing
Computer crashing
Computer restarting
Applications not functioning correctly
Inaccessible disk drives, or a CD-ROM drive that automatically opens and closes
Notification messages that an application has attempted to contact you from the
Internet
Unusual audio sounds
Printing problems
Note that, although these are common signs of infection, these symptoms might also indicate other types of hardware or software
problems that are unrelated to malware.
Signs of a spyware infection tend to be slightly different from those of other types of
malware. If you see any of the following symptoms, suspect spyware:
A new, unexpected application appears.
Unexpected icons appear in the system tray.
Unexpected notifications appear near the system tray.
The Web browser home page, default search engine, or favorites change.
New toolbars appear, especially in Web browsers.
The mouse pointer changes.
The Web browser displays additional advertisements when visiting a Web page, or pop-up
advertisements appear when the user is not using the Web.
When the user attempts to visit a Web page, she is redirected to a completely different
Web page.
The computer runs more slowly than usual.
Some spyware might not have any noticeable symptoms, but it still might compromise private
information.
5. How to Resolve Malware Infections
The most important way to resolve malware infections is to prevent them in the first place
by running antivirus and anti-spyware programs daily with the latest virus and spyware
definitions. If malware is discovered on a system, use the application to remove the malware if
possible and quarantine it if not. If it is a new malware program, you might need to run a
removal tool or perform a series of steps to remove it manually.
These steps naturally apply to malware that is detected. However, as important as it is to
remember to use antivirus and anti-spyware daily, it is just as important to remember that no
anti-malware application is foolproof. Many malware programs are in fact written around
anti-malware software so that they cannot be detected. And if even a single malicious feature
remains after a scan, that remaining malware program can install other malware programs.
If you suspect a problem related to malware after running antivirus and anti-spyware
applications with the latest definitions, take the following steps:
If you notice changes to Windows Internet Explorer, such as unwanted add-ons or a new
home page, use Control Panel to look for and uninstall any unnecessary programs.
Use the Startup tab of the System Configuration utility (Msconfig.exe) to clear any
unnecessary startup programs. Note the Registry entry associated with any of these programs.
(You can use this Registry information to delete the associated Registry keys if necessary.)
Use the Services tab to disable any unnecessary services.
Open Task Manager. Note any unusual services listed on the Services tab or unusual
processes listed on the Processes tab. (Be sure to click Show Processes From All Users so you
can see all running processes.) Use the Go To Process option on the Services tab and the Go
To Service(s) option on the Processes tab to help learn the connection between services and
processes that are unknown to you. Then, perform Web searches on services and processes that
lack descriptions or that otherwise seem suspicious. If you can determine from your research
that any services or processes are associated with malware, right-click them to stop them.
Then, in the Services console, disable the associated service so that it cannot run
again.
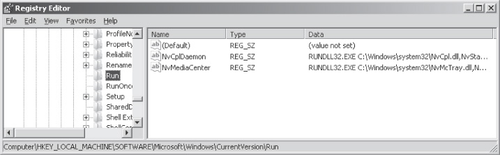
Open the Registry Editor (Regedit.exe). Navigate to
HKLM\Software\Microsoft\Windows\CurrentVersion\Run. In the details pane, note any Registry values associated with unwanted started
programs. Write the path names provided to the target files in the Data column, as shown in
Figure 11, and then delete the Registry
values. Then, navigate to HKCU\Software\Microsoft\Windows\CurrentVersion\Run and do the
same.
Using the path name information that you copied in step 4, visit these locations in the
Windows file structure and delete the target files.
If you still see signs of malware, install an additional anti-spyware and antivirus
application from a known and trusted vendor. Your chances of removing all traces of malware
increase by using multiple applications, but you should not configure multiple applications
to provide real-time protection.
If problems persist, shut down the computer and use the Startup Repair tool to perform a
System Restore. Restore the computer to a date prior to the malware infection. System Restore
typically removes any startup settings that cause malware applications to run, but it does
not remove the executable files themselves. Do this only as a last resort: Although System
Restore does not remove a user's personal files, it can cause problems with recently
installed or configured applications.
Performing this series of steps resolves a great majority of malware problems. However,
once malware has run on a computer, you can never be certain that the software is removed
completely. In particular, rootkits are difficult to detect and remove. In these circumstances, if you suspect
a rootkit and cannot remove it, you might be forced to reformat the hard disk, reinstall
Windows, and then restore user files using a backup created prior to the infection.
5.1. PRACTICE: Enforcing an Anti-Malware Policy Through Group Policy
5.1.1. PRACTICE: Enforcing an Anti-Malware Policy Through Group Policy
In this practice, you use Group Policy to enforce specific settings for UAC and Windows
Defender. These exercises require a domain controller running Windows Server 2008 R2 and a
client running Windows 7 that is a member of the same domain.
EXERCISE 1 Enforcing UAC Settings Through Group Policy
In this exercise, you enforce new UAC default settings on computers running Windows 7 in
the domain.
Log on to the domain controller.
Open Group Policy Management by clicking Start\All Programs\Administrative Tools\Group
Policy Management.
In the Group Policy Management console tree, navigate to Group Policy
Management\Forest: Forest Name\Domains\Domain
Name\Default Domain Policy.
Right-click Default Domain Policy, and then click Edit from the shortcut menu. The
Group Policy Management Editor opens.
In the Group Policy Management Editor, navigate to Default Domain Policy\Computer
Configuration\Policies\Windows Settings\Security Settings\Local Policies\Security
Options.
In the details pane, double-click to open User Account Control: Switch To The Secure
Desktop When Prompting For Elevation.
On the Security Settings tab, click Define This Policy Setting, select Disabled, and
then Click OK.
In the details pane, double-click to open User Account Control: Behavior Of The
Elevation Prompt For Standard Users.
On the Security Settings tab, click Define This Policy Setting, select Prompt For
Credentials from the drop-down list, and then Click OK.
These settings remove the Secure Desktop from all UAC prompts.
Switch to the client running Windows 7. Restart the client, and then log on to the
domain from the client as a domain administrator.
Open an elevated command prompt by clicking Start\All Programs\Accessories, then
right-clicking Command Prompt and clicking Run As Administrator from the shortcut
menu.
A consent prompt appears without a Secure Desktop.
Log off the client, and then log on again to the domain from the client as a standard
user without administrative privileges.
In Control Panel, beneath User Accounts, click Change Account Type. A credential
prompt appears without a Secure Desktop.
EXERCISE 2 Disabling Real-Time Monitoring for Windows Defender
A large corporate network should use a managed anti-spyware solution, which Windows
Defender is not. Using Windows Defender to provide a secondary daily scan for malware on
clients is a good idea, but you should not have two applications performing real-time
monitoring. If your managed anti-spyware solution provides real-time monitoring, you should
disable the same feature on Windows Defender by using Group Policy.
In this exercise, you use Group Policy to disable real-time monitoring for Windows
Defender.
Log on to the domain controller.
Using the steps described in Exercise 1, open Group Policy Management and then choose
to edit the Default Domain Policy.
In the Group Policy Management Editor, navigate to Default Domain Policy\Computer
Configuration\Policies\Administrative Templates\Windows Components\Windows Defender.
In the details pane, double-click to open Turn Off Real-Time Monitoring.
In the Turn Off Real-Time Monitoring dialog box, select Enabled, and then click
OK.
Switch to Client1. Log on to the domain from Client1 as a domain administrator.
Open a command prompt and type gpupdate. You might see
a notification bubble appear indicating that Windows Defender is turned off.
After the command finishes executing, click Start, type windows
defender, and then click Windows Defender in the Start menu.
In Windows Defender, click Tools, and then click Options.
Select Real-Time Protection from the list of options.
The settings are dimmed. Real-time monitoring is disabled.
Return to the domain controller and the Default Domain Policy. Revert the Turn Off
Real-Time Monitoring policy setting to Not Configured, and then click OK.
Rerun gpupdate on Client1, and then close all open
windows on both computers.