The number of new malware applications being released today actually exceeds that of new
legitimate applications. As an enterprise support technician, you need to adequately protect
your clients from these mounting threats and know how to handle malware infections once
they are discovered.
Windows 7 includes two features that assist you in this fight against malware. User Account
Control (UAC) helps prevent programs from secretly altering protected areas of the operating
system, and Windows Defender scans your system for spyware and offers to remove any unwanted
software that is detected.
Though you will need to use additional applications such as Microsoft Forefront and a
managed anti-malware solution to protect your network, understanding how to use and configure
these built-in features of Windows 7 represents part of the essential skill set you need on your
job.
1. Understanding Malware
Malware is an umbrella term for many different types of unwanted software. It's important to understand the nature of these
different threats, but it's also important to recognize that many malware applications blend
features from more than one of these malware types. The following list discusses the most
common types of malware:
Virus
A virus is a self-replicating program that can install itself on a
target computer. Viruses do not propagate over networks automatically; they need to be spread
through e-mail or another means. Once installed, viruses usually alter, damage, or compromise
a system in some way.
Worm A worm is a self-replicating
program that can spread automatically over a network without any help from a user or a
program such as an e-mail client or Web browser. Worms vary greatly in the potential damage
they can cause. Some worms simply replicate and do little other than consume network
bandwidth. Others can be used to compromise a system completely.
Trojan horse A Trojan horse is a program that is presented to users as a desirable
application but that is intentionally written to harm a system. Unlike viruses and worms,
Trojan horses do not copy themselves automatically or install themselves automatically; they
rely on users to install them.
Spyware
Spyware is a type of privacy-invasive software that secretly records
information about user behavior, often for the purposes of market research. Typically spyware
is injected into a system when a user installs a free tool or visits a Web site with browser
security settings set to a low level. The most common function of such spyware is to record
the Web sites that a user visits. More rarely, some spyware, such as keyloggers (which record every keystroke), can be installed deliberately by a
third party and be used to gather personal information. The biggest threat posed by most
spyware is system performance degradation. All types of spyware reduce system performance by hijacking the resources of the
computer for their own purposes. Unlike viruses and worms, spyware does not
self-replicate.
Adware Adware is similar to spyware and is often installed alongside it. The purpose of
adware is to display unsolicited advertisements to the user in the form of pop-up windows or
Web browser alterations. Adware can also download and install spyware.
Note:
SPYWARE AND ADWARE
The term
spyware
is often used as a general term for all unwanted software that runs in
the background and that gathers market research information, displays advertisements, or
alters the behavior of applications such as Web browsers. Microsoft uses the phrase
"spyware and potentially unwanted software" to refer to the type of software that is
unwanted but is not unambiguously harmful.
Backdoor A backdoor is a program that gives a remote, unauthorized party complete control
over a system by bypassing the normal authentication mechanism of that system. Backdoors have
been known to be installed by worms that exploit a weakness in a well-known program. To
protect your system against backdoors, it is essential to keep your applications (not just
your operating system) updated.
Rootkit A rootkit is a persistent type of malware that injects itself beneath the
application level and that as a result, tends to be much harder to detect from within the
operating system. A rootkit can alter the core functionality of the operating system, or it
can install itself as its own operating system invisible to the user and to most anti-malware
software. Other rootkits can operate at the firmware (BIOS) level. Typically, a rootkit is
used to provide a backdoor to a system.
Although malware has been proliferating in type and number, the defenses against these
threats have improved as well. When UAC is enabled in Windows 7, for example, a malware
application cannot install itself easily without the user's knowledge. This next section
provides an overview of UAC, which was introduced in Windows Vista and has been refined in
Windows 7.
2. Understanding UAC
UAC is a set of security features designed to minimize the danger of running
Windows as an administrator and to maximize the convenience of running Windows as a standard
user. In versions of Windows before Windows Vista, the risks of logging on as an administrator
were significant, yet the practice of doing so was widespread. Meanwhile, running as a standard
user was generally safe, but the inconveniences prevented many from adopting the
practice.
In versions of Windows before Windows Vista, malware could use the credentials of a
locally logged-on administrator to damage a system. For example, if you were logged on to
Windows XP as an administrator and unknowingly downloaded a Trojan horse from a network source,
this malware could use your administrative privileges to reformat your hard disk drive, delete
all your files, or create a hidden administrator account on the local system.
The main reason that users in previous versions of Windows often ran as administrators despite these dangers is that many common tasks, such as installing
an application or adding a printer, required a user to have administrator privileges on the local machine. Because in previous versions of
Windows there was no easy way to log on as a standard user and "elevate" to an administrator
only when necessary, organizations whose users occasionally needed administrator privileges simply tended to configure their users as administrators
on their local machines.
Note:
WHAT IS ELEVATION?
The term
elevation
is used when a user adopts administrator privileges to perform a
task.
2.1. How Does UAC Address the Problem of Administrator Privileges?
UAC is the result of a new Windows security design in which both standard users and
administrators use the limited privileges of a standard user to perform most actions. When
users are logged on, UAC prompts them in different ways to confirm actions that make important
changes to the computer. If an administrator is logged on, the action is performed only if he
or she confirms it. If a standard user is logged on, the action is performed only if he or she
can provide administrator credentials. In both cases, the elevation to administrator-level
privileges is temporary and used to perform only the action required. Through this new system,
UAC inhibits malware from secretly using a logged-on administrator's privileges.
2.2. Understanding UAC Notifications for Administrators
By default, UAC is configured to notify administrators only when programs request
elevation. For example, administrators see UAC notification when they attempt to run a program
(such as Cmd.exe) at elevated administrator privileges, as shown in Figure 1. According to this default setting,
administrators in Windows 7 do not see a UAC notification when they adjust Windows settings
that require administrator privileges.
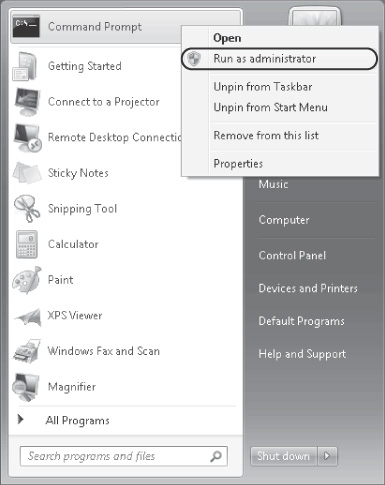
Note:
CHANGES IN WINDOWS 7 UAC BEHAVIOR
For administrators, the default behavior of UAC in Windows 7 has
changed significantly from that in Windows Vista and Windows Server 2008. In those operating
systems, UAC generated a prompt by default whenever any type of elevation was requested,
including when an administrator attempted to change Windows settings. Administrators see UAC
prompts less frequently in Windows 7.
The UAC notification that normally appears for administrators is called a
consent prompt and is shown in Figure 5-2. Note that by default, the entire screen
darkens when the notification appears and freezes until the user responds to the prompt. This
feature is called the Secure Desktop and can be disabled.
Note:
EDUCATE USERS ABOUT UAC PROMPTS!
The point of UAC notifications is to alert users when malware
might be harming your computer. If malware were to request elevation for a particular
purpose, it too would generate a notification such as the one shown in Figures 2 or 3.
Consequently, an essential factor in the ability of UAC to thwart malware is appropriate
user response. You need to educate users—and gently remind your fellow
administrators—that they should click No or Cancel whenever they see a UAC
notification message that they did not initiate.
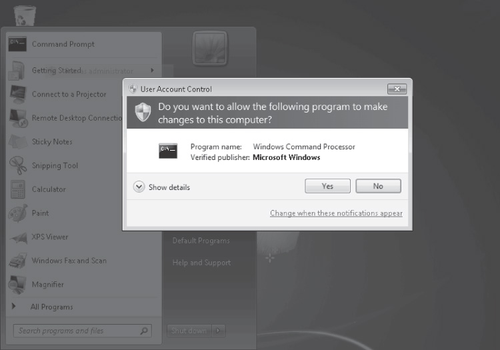
2.3. Understanding UAC Notifications for Standard Users
The UAC notifications shown to standard users are distinct from those shown to
administrators in that the notifications for standard users prompt these users to provide administrator
credentials. As with administrators, standard users by default receive UAC notifications when
they attempt to run a program such as a command prompt at elevated privileges, or when a
program independently requests elevation. In addition, standard users by default receive UAC
notifications when they attempt to make changes on the system that require administrator
privileges. For example, if standard users open the System page in Control Panel and click
Remote Settings, they see the credential prompt shown in Figure 3.
Note:
THE DEFAULT BEHAVIOR OF UAC IS THE SAME FOR STANDARD USERS IN WINDOWS
7
Although UAC in Windows 7 offers many notification levels that did
not exist in Windows Vista or Windows Server 2008, the default behavior for standard users
is the same. Whenever standard users attempt to make a change that requires administrator
privileges, a credential prompt appears on a Secure Desktop.
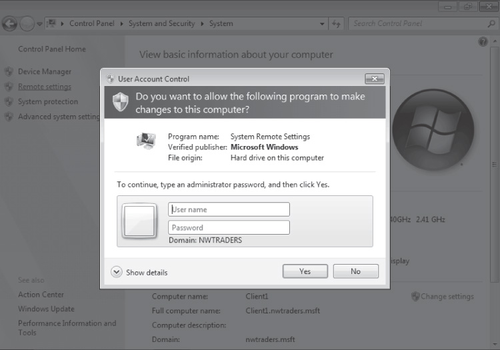
2.4. Configuring UAC in Control Panel
In a domain environment, it is recommended that UAC be controlled centrally by Group
Policy instead of by configuration settings on each local machine. However, in workgroup
environments or in domain environments in which Group Policy allows local UAC configuration, you can configure UAC through Control Panel.
To configure UAC in Control Panel, perform the following steps:
In Control Panel, click System and Security.
Under Action Center, click Change User Account Control Settings, as shown in Figure 4.
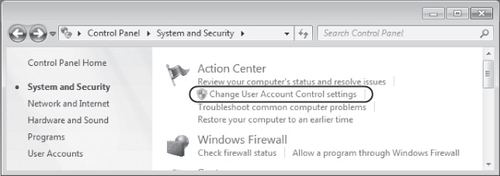
This step opens the User Account Settings window, one version of which is shown in
Figure 5. Note that the set of options
that appears is different for administrators and standard users, and that each user type has
a different default setting.
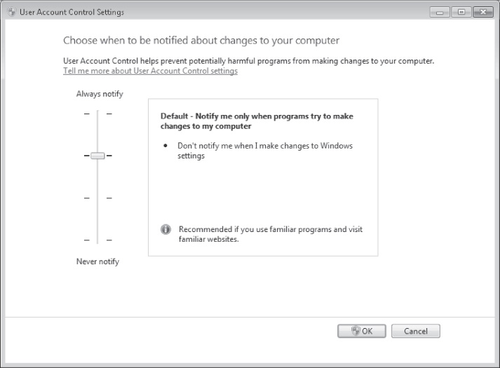
Choose one of the following notification levels:
Always Notify This level is the default for standard
users, and it configures UAC to act as it does in Windows Vista. At this level, users are
notified whenever any changes that require administrator privileges are attempted on the
system.
Notify Me Only When Programs Try To Make Changes To My
Computer This level is the default for administrators and is not available for
standard users. At this level, administrators are not notified when they make changes that
require administrator privileges. However, users are notified through a consent prompt
when a program requests elevation.
Always Notify Me (And Do Not Dim My Desktop) This
level is not available for administrators. It is similar to the
default setting for standard users, except that at this particular level, the Secure
Desktop is never displayed. Disabling the Secure Desktop tends to reduce protection
against malware, but it improves the user experience. This setting might be suitable for
standard users who very frequently need to request elevation.
Notify Me Only When Programs Try To Make Changes To My Computer
(Do Not Dim The Desktop) This level is available for both standard users and
administrators. At this level, the behavior is the same as with the default administrator
level ("Notify me only when programs try to make changes to my computer"), but with this
option the Secure Desktop is not displayed.
Never Notify This level disables notifications in
UAC. Users are not notified of any changes made to Windows settings or when
software is installed. This option is appropriate only when you need to use programs that
are incompatible with UAC.
2.5. Configuring UAC Through Group Policy
You can configure UAC through Local Security Policy or Group Policy settings. To find UAC-related policy settings in a GPO, navigate to
the following node:
Computer Configuration\Policies\Windows Settings\Security Settings\Local
Policies\Security Options
This location is shown in Figure 6.
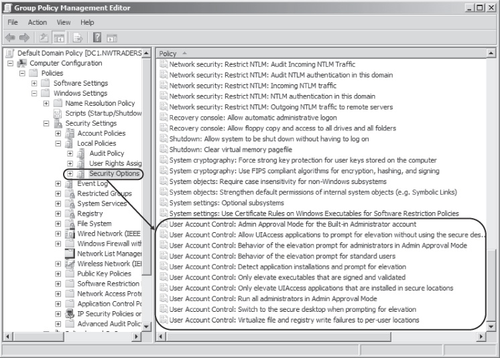
The following 10 UAC-related policy settings are available. The next section describes
each of these configurable settings.
User Account Control: Admin Approval Mode For The Built-in
Administrator Account This policy applies only to the built-in Administrator account, and not to
other accounts that are members of the local Administrators group. When you enable this
policy setting, the built-in Administrator account sees UAC notifications just as other administrative accounts do. When you disable the
setting, the built-in Administrator account behaves just like it does in Windows XP, and all
processes run using Administrator privileges. This setting is disabled in Local Security
Policy by default.
User Account Control: Allow UIAccess Applications to Prompt For Elevation Without Using The Secure Desktop This setting controls whether user Interface Accessibility (UIAccess) programs
can disable the Secure Desktop automatically. When enabled, UIAccess applications (such as
Remote Assistance) automatically disable the Secure Desktop for elevation prompts. Disabling
the Secure Desktop causes elevation prompts to appear on the standard desktop. By default,
this setting is disabled in Local Security Policy.
User Account Control: Behavior Of The Elevation Prompt For
Administrators In Admin Approval Mode This policy setting controls the behavior of
the elevation prompt for administrators. Six options are available:
Elevate Without Prompting With this option,
administrators never see elevation prompts.
Prompt For Credentials On The Secure Desktop When this
option is chosen, administrators see credential prompts on a Secure Desktop when elevation
is requested.
Prompt For Consent On The Secure Desktop With this
option, administrators see a consent prompt on a Secure Desktop when elevation is
requested.
Prompt For Credentials When this option is selected,
administrators see a credential prompt on a normal desktop when elevation is
requested.
Prompt For Consent When this option is selected,
administrators see a consent prompt on a normal desktop when elevation is
requested.
Prompt For Consent For Non-Windows Binaries This
option is the default setting in Local Security Policy. It causes a consent prompt to
appear any time an application requests elevation.
User Account Control: Behavior Of The Elevation Prompt For
Standard Users This policy setting controls the behavior of the elevation prompt
for standard users. Three options are available:
Automatically Deny Elevation Requests When this option
is enforced, standard users are not able to perform tasks that require elevation.
Prompt For Credentials On The Secure Desktop With this
option (the default setting in Local Security Policy), standards users see a credential
prompt on the Secure Desktop when elevation is requested.
Prompt For Credentials When this option is chosen,
standard users see a credential prompt on the normal desktop whenever elevation is
requested.
User Account Control: Detect Application Installations And Prompt
For Elevation When enabled, this policy setting configures UAC to prompt for administrative credentials when the user attempts to install
an application that makes changes to protected aspects of the system. When disabled, the
prompt won't appear. Domain environments that use delegated installation technologies such
as Group Policy Software Install (GPSI) or Microsoft Systems Management Server (SMS) can
disable this feature safely because installation processes can escalate privileges
automatically without user intervention. By default, this setting is enabled in Local
Security Policy.
User Account Control: Only Elevate Executables That Are Signed
And Validated When this policy setting is enabled, Windows 7 refuses to run any
executable that isn't signed with a trusted certificate, such as a certificate generated by
an internal Public Key Infrastructure (PKI). When disabled, this policy setting allows users
to run any executable, potentially including malware. If your environment requires all
applications to be signed and validated with a trusted certificate, including internally
developed applications, you can enable this policy to increase security greatly in your
organization. This setting is disabled in Local Security Policy by default.
User Account Control: Only Elevate UIAccess Applications That Are
Installed In Secure Locations When enabled, this policy setting causes Windows 7 to grant user interface
access only to those applications that are started from Program Files or subfolders, from
Program Files (x86) or subfolders, or from \Windows\System32\. When disabled, the policy
setting grants user interface access to applications regardless of where they are started in
the file structure. This policy setting is enabled by default in Local Security
Policy.
User Account Control: Run All Administrators In Admin Approval
Mode This policy setting, enabled by default in Local Security Policy, causes all
accounts with administrator privileges except for the local
Administrator account to see consent prompts when elevation is requested. If you disable
this setting, administrators never see consent prompts and the Security Center displays a
warning message.
User Account Control: Switch To The Secure Desktop When Prompting
For Elevation The Secure Desktop is a feature that darkens the screen and freezes all
activity except for the UAC prompt. It reduces the possibility that malware can function,
but some users might find that the feature slows down their work too much. When enabled,
this policy setting causes the Secure Desktop to appear with a UAC prompt. When disabled,
this policy setting allows UAC prompts to appear on a normal desktop. This policy setting is
enabled by default in Local Security Policy.
User Account Control: Virtualize File And Registry Write Failures
To Per-User Locations This policy setting, enabled by default in Local Security
Policy, improves compatibility with applications not developed for UAC by redirecting
requests for protected resources. When disabled, this policy setting allows applications not
developed for UAC to fail.
2.6. Disabling UAC Through Local or Group Policy
To force UAC to a disabled state, you can use Local Security Policy or Group Policy.
First, set the User Account Control: Behavior Of The Elevation Prompt For Administrator In
Admin Approval Mode setting to Elevate Without Prompting. Then, disable the User Account
Control: Detect Application Installations And Prompt For Elevation and User Account Control:
Run All Administrators In Admin Approval Mode settings. Finally, set User Account Control:
Behavior Of The Elevation Prompt For Standard Users setting to Automatically Deny Elevation
Requests. Then, restart the computers on which you want to apply the new settings.
2.7. Best Practices for Using UAC
To receive the security benefits of UAC while minimizing the costs, follow these
best practices:
Leave UAC enabled for client computers in your organization.
Have all users—especially IT staff—log on with standard user
privileges.
Each user should have a single account with only standard user privileges. Do not give
standard domain users accounts with administrator privileges to their local
computers.
Domain administrators should have two accounts: a standard user account that they use
to log on to their computers, and a second administrator account that they can use to
elevate privileges.
Train users not to approve a UAC prompt if it appears
unexpectedly. UAC prompts should appear only when the user is installing an application or
starting a tool that requires elevated privileges. A UAC prompt that appears at any other
time might have been initiated by malware. Rejecting the prompt helps prevent malware from
making permanent changes to the computer.
Whereas UAC is a set of features that broadly aims to protect core areas of the operating
system, another Windows 7 tool—Windows Defender—has a much narrower goal of detecting and removing
unwanted software.