1. Problem
You need to guarantee that
only the intended recipient of a message can understand it by encrypting
the message. The recipient needs to verify the message sender by
checking a digital signature included with the message.
2. Solution
You can implement an
encryption mechanism for outgoing messages, as well as a decryption
mechanism for the inbound messages. As an example, suppose that you need
BizTalk to send this message shown in Listing 4-1
across the Internet to move the requested amount of money between the
specified accounts. This message contains sensitive information,
including bank account numbers and a Social Security number.
Example 1. Sensitive Information
<ns0:MoneyTransfer xmlns:ns0="http://Creating_EncryptionPipelines.Confidential">
<TransferAmount>108.37</TransferAmount>
<TransferInitDate>2005-09-30</TransferInitDate>
<FromAccount>0987-654-321</FromAccount>
<ToAccount>1234-567-890</ToAccount>
<RequestedBySSN>123-45-6789</RequestedBySSN>
<RequestedByName>StacyR</RequestedByName>
</ns0:MoneyTransfer>
|
BizTalk sends the message with the encryption pipeline constructed in this recipe. The message becomes encrypted, as shown in Listing 4-2. No one but the intended recipient can understand the message.
Example 2. Encrypted Message
Content-ID: {51572541-E6CE-4DD6-913C-B7C7558D2269}
Content-Description: body
Bcc:
MIME-Version: 1.0
Content-type: application/x-pkcs7-mime; smime-type=enveloped-data; name="smime.p7m"
Content-Transfer-Encoding: base64
MIAGCSqGSIb3DQEHA6CAMIACAQAxgbwwgbkCAQAwIjAUMRIwEAYDVQQDEwlkZXZvbmx5Y2ECCmEI
BAMAAAAAAAIwDQYJKoZIhvcNAQEBBQAEgYAH+kU66z4r4lZYzq1eOKNf0Yt1HVMBaYL61W5wrTPt
...
qQ+ubHBbgHMXyJl/SPylOtSN9XeQGZgBGKb2j+MeB0NEjHlRE22aDnazailnmgu2x588820wnQAA
AAAAAAAAAAA=
|
The message
recipient decrypts the message with the decryption pipeline constructed
in this recipe, obtaining the same message as before encryption (see Listing 1).
The following sections show how to enable message encryption and decryption.
3. Send an Encrypted Message
To implement an
encryption mechanism for outgoing message, follow these steps on the
BizTalk Server responsible for encrypting the message and sending it:
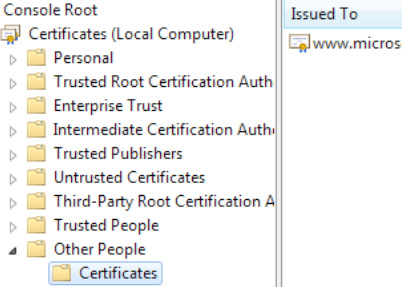
Obtain the public key certificate from the party that will securely receive the message, and install it in the Local Computer\Other People folder, as shown in Figure 1.
NOTE
BizTalk provides
native support for MIME encryption decryption using X.509 version 3
certificates. Microsoft Certificate Services can generate the
certificates used by BizTalk.
NOTE
The certificate store can be opened by typing mmc at a command prompt. Click File => Add/Remove Snap-in.
Create an empty BizTalk solution, and add a new send pipeline to the solution (right-click the project, select Add => New Item, and select Send Pipeline from the Add New Item dialog box). Give the send pipeline an appropriate name.
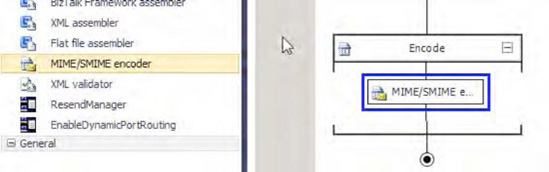
Drag
the MIME/SMIME Encoder component from the BizTalk Pipeline Components
section of the toolbox to the Encode stage of the send pipeline, as
shown in Figure 2.
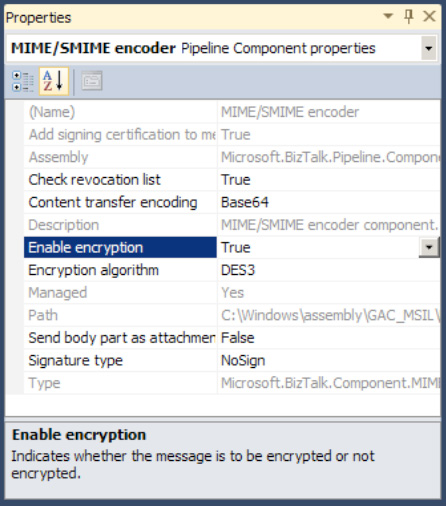
Right-click the encoder in the pipeline, and select Properties. Change the value of the Enable encryption property to True, as shown in Figure 3.
Build and deploy the BizTalk project containing the send pipeline.
Create a send port to deliver the message to the recipient, using any transport adapter desired.
In
the Send section of the Send Port Properties dialog box, select the
send pipeline with the MIME/SMIME encoder component. Then select the
public-key certificate of the message receiver for the Certificate Name property.
4. Receive an Encrypted Message
To configure a
decryption mechanism for an incoming message, follow these steps on the
BizTalk Server responsible for decrypting the message upon receipt:
Obtain a certificate from a certification authority (CA) containing a private key.
Log
in to the BizTalk Server with the BizTalk service account credentials.
Open the certificate file containing the private key, and install it
into the Current User\Personal\Certificates folder of the BizTalk service account.
Create an empty BizTalk solution, and add a new receive pipeline to the solution (right-click the project, select Add => New Item, and select Receive Pipeline from the Add New Item dialog box).
Drag
the MIME/SMIME Decoder component from the BizTalk Pipeline Components
section of the toolbox to the Decode stage of the receive pipeline, as
shown in Figure 4.
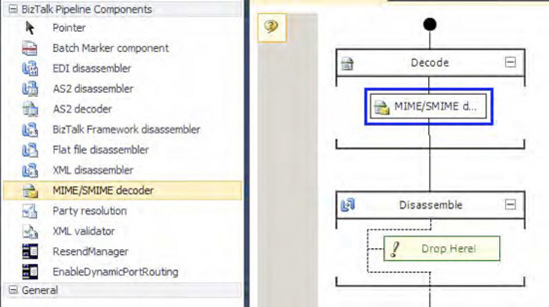
Build and deploy the BizTalk project containing the receive pipeline.
Create
a receive port and a receive location to accept the encrypted message
from the sender, using any desired transport adapter.
In the Receive Location Properties dialog box, specify the receive pipeline with the MIME/SMIME decoder, as shown in Figure 5.
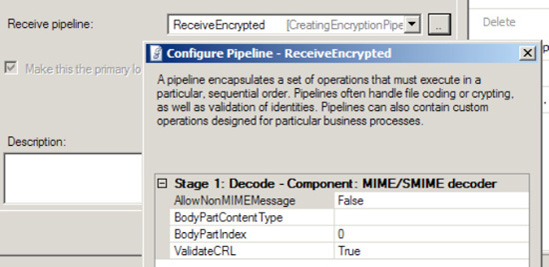
Using
the BizTalk Administration Console, open Platform Settings and select
Host Instances. Right click the BizTalk host that will receive the
encrypted message and select Properties.
Specify
the decryption certificate BizTalk will use to receive messages. Secure
messages by pasting the thumbprint of the certificate containing the
private key into the Thumbprint field in the Certificates section of the
Host Properties dialog box.
5. How It Works
Organizations
often deal with confidential information that only the message sender
and recipient should understand. For example, financial information may
contain sensitive information such as Social Security or bank account
numbers. Medical information may contain private information protected
by law. Use the encryption capabilities of BizTalk to protect the
confidentiality of sensitive information, while still allowing two
parties to share it easily.
BizTalk can transmit encrypted
information across a network securely. This is particularly important
when transmitting messages over a public network, such as the Internet.
If the two parties must keep the message confidential, encryption can
ensure only the intended recipient can understand it.
One option for ensuring the
confidentiality of messages is to use a secure transport like HTTPS.
Securing the message transport can be effective, but the transport
generally secures only communication directly between two machines on a
network. When a message has several network hops before it arrives at
the final destination, each hop must be secured individually, providing
multiple chances for a configuration error to expose the sensitive
information. For example, HTTPS may securely transmit a message to a
trading partner, but then be transmitted without encryption over an
insecure transport within the trading partner's internal network. To
ensure a higher level of confidentiality, you should encrypt the
contents of the message, rather than depend on the communication
protocol. Message content encryption provides confidentiality over any
transport, including transports or BizTalk adapters that cannot support
encryption, such as the FTP and SMTP adapters.
BizTalk's
encryption capabilities use certificates containing cryptographic key
pairs of a public key and a private key. The owner of a certificate can
share the public key freely with anyone who wants to send the owner
confidential information. However, only the certificate's owner should
know its private key.
To encrypt a message,
the sender obtains the public key of the message recipient and applies
an encryption algorithm to the message. The recipient uses the
corresponding private key and the same algorithm to decrypt and
understand the message. Certificate owners must fiercely protect private
keys because anyone who possesses a private key can decrypt messages
encrypted with the corresponding public key. However, certificate owners
must distribute public keys to anyone who wishes to send an encrypted
message.
BizTalk can securely transmit
information to many recipients, using a different certificate for each
recipient. BizTalk will detect all certificates placed in the Local Computer\Other People
certificate store of the local machine. For example, if you have
several trading partners that you must securely exchange information
with over the Internet, you can configure a different send port for each
trading partner and specify a different public key certificate in each
send port.
The decryption certificate must
be in the private store of the BizTalk service account receiving
encrypted messages. While BizTalk can use any number of public keys to
send encrypted information, each BizTalk host can have only one
decryption certificate. Each certificate contains a unique identifier
called a thumbprint,
which BizTalk uses to identify the correct certificate from this store
to decrypt messages. The thumbprint is calculated by applying a hashing
algorithm to the certificate.
In addition to encryption,
BizTalk can also add a digital signature to encrypted messages. The
message recipient can verify the signature using the sender's public key
to be guaranteed that the message originated with the original sender
and was not modified while in transit. To enable message signing, set
the Signature type property of the MIME/SMIME encoder component, as shown in Figure 6.
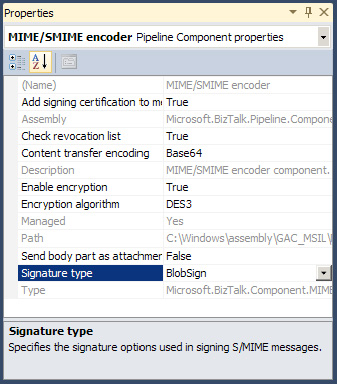
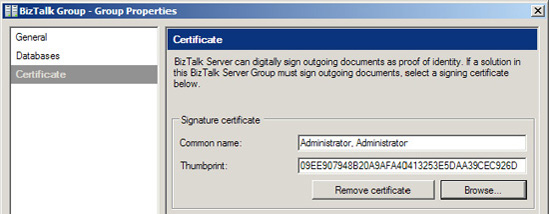
While each
BizTalk host can have a unique decryption certificate, an entire BizTalk
group can have only one signing certificate. Specify the signing
certificate by entering the thumbprint of the certificate in the Group
Properties dialog box for the BizTalk group, as shown in Figure 7. This can be accessed by right-clicking the BizTalk Group in BizTalk Administration Console and selecting Properties.