The ancillary mail services of
the Post Office Protocol version 3 (POP3) and Internet Message Access
Protocol version 4 (IMAP4) can be secured through an ISA server. This is
particularly important for organizations that require support of these
legacy protocols; they are less secure than the newer forms of mail
access available.
Creating and
Configuring a POP Mail Publishing Rule
POP3 servers are secured in
ISA through the creation of a special rule that enables ISA to examine
all traffic sent to the POP3 server and perform intrusion detection
heuristics on it with an advanced POP intrusion detection filter. The
POP server does not necessarily need to be a Microsoft server, such as
Exchange Server, but can be run on any POP3-compliant messaging system.
Caution
Enable POP support in a
messaging environment only if there is no other viable option. POP3
support is less secure than other access methods, and can cause mail
delivery and security issues. For example, many POP clients are
configured to pull all the mail off the POP server, making it difficult
to do disaster recovery of mail data.
After a POP server has
been enabled or established on the internal network, it can be secured
via modification of an existing rule or creation of a new rule to secure
POP traffic as follows:
1. | From the ISA console, select the Firewall Policy node
from the console tree.
|
2. | In the tasks pane, click the Publish Mail Servers link.
|
3. | Enter a descriptive name for the rule (for example, POP
Access), and click Next.
|
4. | Select the Client Access: RPC, IMAP, POP3, SMTP option,
and click Next.
|
5. | In the
Select Services dialog box, select POP3 (Standard port), and click Next.
|
6. | Enter the internal IP address of the POP server, and
click Next.
|
7. | Select to
which networks the ISA server will listen by checking the boxes next to
them, and click Next.
|
8. | Click Finish, click Apply, and then click OK.
|
Note
By default,
enabling a POP publishing rule turns on the POP intrusion detection
filter, which can help protect a POP system from potential exploits.
That said, POP3 is still an insecure protocol, and it is preferable not
to deploy it on a server.
Creating and
Configuring an IMAP Mail Publishing Rule
The Internet Message Access
Protocol (IMAP) is often used as a mail access method for UNIX systems
and even for clients such as Outlook Express. It also can be secured
through an ISA server, using the same rule as a POP rule, or through the
configuration of a unique IMAP publishing rule.
After the
internal IMAP presence has been established, an ISA rule can be created
to allow IMAP traffic to the IMAP server. The following procedure
outlines this process:
1. | From the ISA console, select the Firewall Policy node
from the console tree.
|
2. | In the tasks pane, click the Publish Mail Servers link.
|
3. | Enter a descriptive name for the rule (for example,
IMAP Access), and click Next.
|
4. | Click the Client Access:
RPC, IMAP, POP3, SMTP option button, as shown in Figure 1, and click Next.
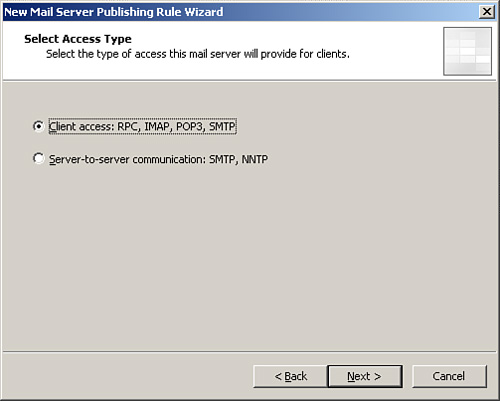
|
5. | In the
Select Services dialog box, select Secure Ports for IMAP4, and click
Next.
|
6. | Enter the
internal IP address of the POP server, and click Next.
|
7. | Select to which networks the ISA server will listen by
checking the boxes next to them, and click Next.
|
8. | Click Finish.
|