Installing server roles, with proper planning, on a
Windows Server 2008 R2 server can be a fairly straightforward process.
But even with the proper planning, sometimes your server roles can be
made to run more efficiently. You may also want to make sure your
servers and the roles installed on the servers are running properly.
When you install a server, you
usually have planned out how it will fit the needs of your business and
your network infrastructure. However, what happens when you are not in
control and you "inherit" servers from a new customer, from an
acquisition, or because you took a new role in your organization? How do
you know if the servers and roles are running properly? In the
following sections, you will learn about a tool called the Best
Practices Analyzer (BPA) that will provide you with guidance to help run
your servers more efficiently.
1. Understand the Best Practices Analyzer
Microsoft has provided the
Best Practices Analyzer for several years for the various server
platforms currently available. These analyzers were available through a
free download from the Microsoft site. With Windows Server 2008 R2, the
Best Practices Analyzer is now built in to the server platform and is
available for you to use when you install certain roles on your server.
Currently in Windows Server 2008 R2, the BPA is provided only for the
following roles:
Active Directory Certification Services (AD CS)
Active Directory Domain Services (AD DS)
DNS
Remote Desktop Services (RDS)
Internet Information Services (IIS)
The BPA is like a mini IT
consultant running around your Windows Server 2008 R2 server and
checking your roles to make sure the ones on your server are running
properly. This tool provides you with the ability to manage your servers
proactively and get in front of any potential issues or concerns before
they happen. The BPA helps you make sure your configurations are good
and helps reduce the amount of troubleshooting you have to do when
issues do occur.
When you use the BPA, it will
analyze your current environment and compare this against common best
practices for the particular role. What makes the guidance from the tool
unique is that Microsoft is not the only one providing feedback; the
feedback comes from IT administrators and customers like yourself, from
support professionals, and even from the many folks in the field working
for Microsoft.
When you invoke a BPA scanner
against one of your server roles, you start the BPA runtime. The runtime
is the main process responsible for collecting and comparing the
configuration settings on your Windows Server 2008 R2 server. Regardless
of which role you are currently scanning, the BPA follows the process
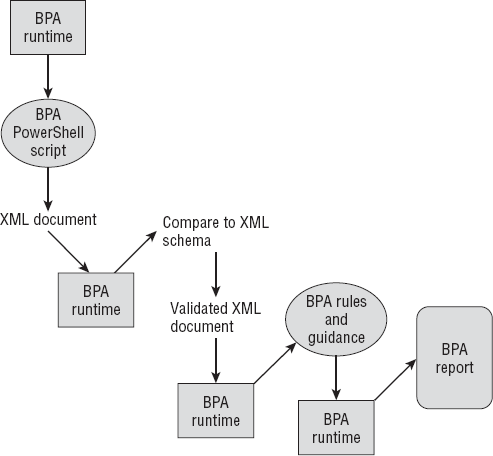
illustrated in Figure 1.
The BPA scans and verifies the current role configuration settings.
As
the BPA service scans and verifies, the BPA runtime uses a BPA Windows
PowerShell script to collect configuration data and store it in an XML
document.
The
BPA runtime then validates the XML document against an XML schema. The
schema defines the format and structure of the XML document.
The
BPA runtime then applies the BPA rules (these are the best-practice
configurations) for the environment against the XML document.
From
there the guidance is used to produce the BPA report. The report is
used to help make adjustments to your environment if needed.
When you first review a
report, you may see violations in the report. You do not need to panic
when you see violations in your BPA report. These violations do not
always indicate a major problem for your server. Remember, the BPA tool
is trying to help identify for you server configurations that can result
in poor performance, poor reliability, unexpected conflicts, increased
security risks, or other potential problems.
Although the guidance in the
tool can be a tremendous help in reporting your actual configuration vs.
the known best practices, you should always look carefully at the
suggestions. The best practices are sound; however, sometimes based on
your business rules and the demands of your infrastructure, they may not
improve your configuration. So, review the recommendations very
carefully.
2. Use the Best Practices Analyzer
The BPA is located in Server
Manager and becomes available after you install the supported roles. You
will find the BPA on the role summary screen for the supported roles on
your server. The summary screen for the roles provides a wealth of
information for your server, and if the role has a BPA available, you
will see it there.
Open Server Manager by selecting Start => Administrative Tools and clicking Server Manager.
Click the + sign next to Roles in the tree menu on the left to expand the roles.
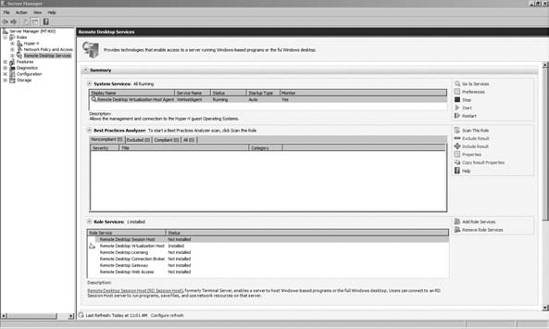
Click the role you want to scan, and you will see a role summary screen similar to Figure 2.
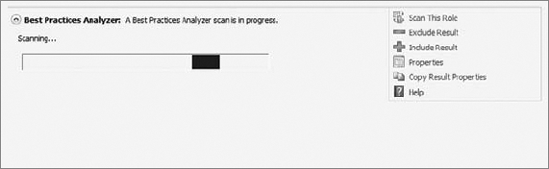
Next
to Best Practices Analyzer, click Scan This Role, and you will see the
BPA process begin to scan your selected role, as shown in Figure 3. The scan could take several minutes.
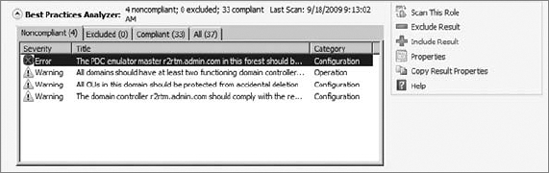
After the scan is complete, you will see the BPA report, as shown in Figure 4.
2.1. Understand the BPA Report
When you create a BPA report, it
considers several factors for your server role. For example, when you
run an AD DS BPA scan, the analyzer is checking these aspects of your
configuration:
DNS rules
Operation master connectivity rules
Operation master ownership rules
Number of controllers in the domain
Required service rules
Replication configuration rules
W32time configuration rules
Virtual machine configuration rules
You can view all the rules scanned for the different roles at http://technet.microsoft.com/en-us/library/dd392255(WS.10).aspx
As you can see, the scan is
very thorough. Regardless of what scan you run, you will see several
aspects of the report on the summary screen. Your report will have one
of three severity levels for each rule. The three levels of severity for
the scanned rules are as follows:
Non-Compliant (indicated by an X in a red circle) This means your scanned role is not compliant with the particular BPA rule scanned.
Warning (indicated by an ! in a yellow triangle)
This means your current role is compliant, but your current
configuration of the role does not meet all the conditions specified by
the rule. In general, this means your role will work; however, there may
indications the role is not fully functional.
Compliant (indicated by a  in a green circle) This means your scanned role is compliant with the particular BPA rule scanned.
in a green circle) This means your scanned role is compliant with the particular BPA rule scanned.
In addition to the
severity level, each rule is categorized into one of eight categories.
The categories are designed to help you further target and work with the
BPA report. In a sense, the categories, as listed in Table 1, help you prioritize the tasks you will need to take action on.
Table 1. BPA Rule Categories
| Category | Definition |
|---|
| Security | These rules help you examine the areas of your server with potential security risks; you'll want to pay close attention to them. |
| Performance | These
rules are designed to help you tune or improve the performance of your
servers. These rules help to make sure your server can perform the
appointed tasks properly. |
| Configuration | These
rules allow you to verify the configurations of certain roles on your
server. These help the role(s) run properly and free of configuration
errors. |
| Policy | These
rules identify which areas in the registry or Group Policy need
improvements to make sure your role is running in a secure and
best-possible fashion. |
| Operation | These rules will identify whether a role is failing and how to correct the role to get it up and running properly. |
| Pre-deployment | These rules allow you to identify any issues or possible errors prior to the deployment of a particular role in the enterprise. |
| Post-deployment | These rules allow you to identify any issues or possible errors after the role has been deployed to the enterprise. |
| BPA Prerequisites | These
rules are for the BPA scanner. In order for certain BPA rules to be
included in a report, there may be some prerequisites that need to be
met in order for a rule to be scanned. If you have a BPA prerequisite
error, this simply means the BPA tool could not scan your role with a
particular rule. |
2.2. Work with the BPA Report
Now that you understand
how the report is categorized, you will want to see how to fix any
issues the BPA scan detected for you. After the report is processed and
you have identified the events you want to view, you will start to see
the power behind the BPA reports. Each rule has properties you can view
that will tell you what violated the BPA rule. The properties of the
report are broken into three sections: what the issue is, what is the
impact of the violation, and most important what the resolution is. To
see this information, you need to view the properties of the rule:
In the BPA report, click the rule you want to view.
To
view the properties, you can either double-click the rule, right-click
the rule and select Properties, or click Properties to the right of the
BPA report. After you have done this, you will see a Properties dialog
box similar to Figure 5.
When you are done viewing the information, click Close.
You also have the ability to
exclude your BPA rule information from future reports. With a rule
highlighted, you can click Exclude This Item, and it will be removed
from the report. It will be moved to the Excluded tab of the report.
As you can see, the BPA
reports provide some excellent analysis for your server. After you have
viewed the error messages and corrected any errors, you should also
consider rerunning the BPA for the role to verify the issue has been
properly resolved.
