Managing the configuration and settings of domain
servers and workstations can be standardized using domain group
policies. Domain group policies offer the advantage of taking user error
and mistakes out of the loop by pushing out the configuration and
security of computers from a single or a set of group policies. Of
course, with this much control it is essential that group policies are
tested and tested again to verify that the correct configuration and
desired results are achieved with the policies. In the early days of
Active Directory domain based group policies, a few organizations, which
will go unnamed in this book, found themselves locked out of their own
computers and Active Directory domain controllers because of
overrestrictive Group Policy security settings and application of these
settings to all computers and users, including the domain
administrators. When this situation occurs, a domain controller can be
rebooted into Directory Services Restore mode and an authoritative
restore of Active Directory might be required.
Before domain group
policies can be created and managed, the Group Policy Management Console
needs to be installed. Also, if printers will be installed using the
Deploy Printer function of Group Policy, the Print Services Tools should
also be installed. To install the GPMC and Print Services Tools,
perform the following steps:
1. | Log on to a designated administrative system running Windows Server 2008 R2.
| 2. | Open Server Manager from the Administrative Tools menu.
| 3. | After Server Manager loads, click on the Features node in the tree pane.
| 4. | Select Add Features in the right pane.
| 5. | Scroll down and check the box next to Group Policy Management.
| 6. | Expand Remote Server Administration Tools and expand Role Administration Tools.
| 7. | Check the box next to Print and Document Services Tools and click Next.
| 8. | Confirm the selection and click Install to begin the process.
| 9. | After the process completes, click Close to complete the installation.
|
Creating a New Domain Group Policy Object
To create a new domain Group Policy Object, perform the following steps:
1. | Log on to a designated Windows Server 2008 R2 administrative server.
| 2. | Click Start, click All Programs, click Administrative Tools, and click on Group Policy Management.
| 3. | If necessary, expand the forest node, the domains node, and the correct domain.
| 4. | Right-click the Group Policy Objects container, and select New.
| 5. | Type in a name for the new GPO.
| 6. | If
the starter GPO functionality in the domain is enabled and if a
suitable starter GPO exists, click the Source Starter GPO drop-down list
arrow, and select either (None) or the desired starter GPO.
| 7. | Click
OK to create the GPO. In the tree pane of the Group Policy Management
Console window, expand the Group Policy Objects container to reveal the
newly created GPO.
| 8. | After the GPO is created, it can be edited by right-clicking on the GPO and selecting Edit.
| 9. | Close the Group Policy Management Console and log off of the server.
|
Creating and Configuring GPO Links
After a GPO is created and
configured, the next step is to link the GPOs to the desired Active
Directory containers. To link an existing GPO to an Active Directory
container, perform the following steps:
1. | Log on to a designated Windows Server 2008 R2 administrative server.
| 2. | Click Start, click All Programs, click Administrative Tools, and click on Group Policy Management.
| 3. | Add the necessary domains or sites to the GPMC as required.
| 4. | Expand the Domains or Sites node to expose the container to which the GPO will be linked.
| 5. | Right-click the desired site, domain, or organizational unit, and select Link an Existing GPO.
| 6. | In the Select GPO window, select the desired domain and GPO, and click OK to link it.
|
Managing User Account Control Settings
Windows 7, Windows Vista,
Windows Server 2008, and Windows Server 2008 R2 contain a security
feature called User Account Control (UAC). UAC was created primarily to
reduce or prevent unauthorized changes to the operating system
configuration or file system. UAC interacts with both nonadministrators
and administrators in their desktop environment and runs almost all
applications in Standard User mode. When an administrator, regular user,
or application attempts to perform an action that can result in a
system configuration change or require access to sensitive areas of the
operating system or file system, UAC interrupts the change and prompts
for authorization or credentials to validate the change or requested
access or elevation desired by the end user.
UAC settings are pretty flexible
in allowing applications to run as desired but can require some tuning
on the part of the desktop administrator. Many independent software
vendors have been able to produce applications that can interact with
UAC but in some cases where functionality or usability of a PC is
impacted by UAC, some administrators or organizations may decide to
disable UAC completely or just certain UAC settings to optimize the user
experience. For situations when UAC is causing undesired issues with
applications, if adjusting file security, user rights assignments, or
running applications in legacy XP mode do not work, it might be
necessary to adjust or disable User Account Control settings. The likely
candidates are applications that formerly required the end user to be a
member of the local Power Users or Administrators group. UAC settings
should not adversely affect the functionality and operation of standard
users. On the contrary, UAC actually allows standard users to be
prompted for credentials to allow elevation of rights to install
software or components that would have failed with previous operating
systems with an Access Denied message. If, for some reason, the end user
requires local administrator rights to run a legacy application and all
other options have failed, then changing UAC security settings in a
local computer policy or domain group policy object is required. When
UAC security setting changes are required, perform the following steps:
1. | Log on to a designated Windows Server 2008 R2 administrative server.
| 2. | Open the Group Policy Management Console from the Administrative Tools menu.
| 3. | Add the necessary domains to the GPMC as required.
| 4. | Expand the Domains node to reveal the Group Policy Objects container.
| 5. | Either create a new GPO or edit an existing GPO.
| 6. | After
the GPO is opened for editing in the Group Policy Management Editor,
expand the Computer Configuration node, expand the Policies node, select
the Windows Settings node, and expand it.
| 7. | Expand the Security Settings node, expand Local Policies, and select Security Options.
| 8. | In
the Settings pane, scroll to the bottom of the pane to locate the UAC
settings. The following list displays the default UAC settings in the
Local Computer Policy for Windows Server 2008 R2:
- Admin Approval Mode for the Built-In Administrator Account— Disabled
- Allow UIAccess Applications to Prompt for Elevation Without Using the Secure Desktop— Disabled
- Behavior of the Elevation Prompt for Administrators in Admin Approval Mode— Prompt for consent for non-Windows binaries
- Behavior of the Elevation Prompt for Standard Users— Prompt for credentials
- Detect Application Installations and Prompt for Elevation— Enabled
- Only Elevate Executables That Are Signed and Validated— Disabled
- Only Elevate UIAccess Applications That Are Installed in Secure Locations— Enabled
- Run All Administrators in Admin Approval Mode— Enabled
- Switch to the Secure Desktop When Prompting for Elevation— Enabled
- Virtualize File and Registry Write Failures to Per-User Locations— Enabled
| 9. | To
disable all UAC functionality using domain policies, create and link a
new GPO for UAC and edit the setting named Run All Administrators in
Admin Approval Mode, and configure the setting value to Disabled. If
this setting is configured as Disabled, all other UAC settings are
ignored. Also, this setting change will be applied during startup,
shutdown, and background refresh, but a reboot will be required to
complete the setting change.
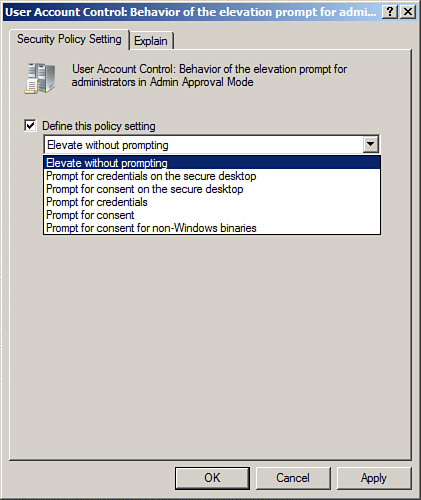
| 10. | To
disable UAC prompts when logged on with an account with Local
Administrator rights and leave all other settings functional, using
domain policies, create and link a new GPO for UAC and edit the setting
named Behavior of the Elevation Prompt for Administrators in Admin
Approval Mode, and configure the setting value to Elevate Without
Prompting, as shown in Figure 1. Click OK to save the setting and close the Group Policy Management Editor window.
| 11. | After
the GPO is configured as desired, save the GPO and link it to an
organizational unit that has a test Windows Vista, Windows 7, Windows
Server 2008, or Windows Server 2008 R2 system to verify that the desired
functionality has been achieved.
| 12. | After
the testing is completed, configure security filtering and possibly
also WMI filtering to limit the application scope of this policy and
link it to the desired organizational unit(s). |
|