Creating Application Control Policies (AppLocker)
Application
control policies are new for Windows 7 Enterprise and Ultimate Editions
and all editions of Windows Server 2008 R2. Application control
policies are similar in function to software restriction policies but
they should not be deployed in the same policy that has software
restriction policies defined. As a best practice, configure policies
with application control policies to be processed by machines only
running Windows 7 Enterprise and Ultimate operating systems and/or
Window Server 2008 R2 systems.
Application control
policies or AppLocker, when enabled, will not allow users to run any
executables except those defined as allowed. This can, of course, cause
serious functionality issues if deployed improperly, so Microsoft has
developed an audit-only mode that can be used to test a policy with
AppLocker settings to start gathering a list of applications end users
need to run to perform their job.
Before AppLocker policies can
function and be applied to the desired Windows 7 and Windows Server 2008
R2 systems, the Application Identity service needs to be running. This
service can be set to automatic startup on the desired systems by
configuring and applying domain policies. To configure this service to
automatic startup on the desired systems, create a new domain policy and
in the Computer Configuration node beneath Windows Settings and System
Services, locate the Application Identity service, define the policy
setting, and set the startup mode to Automatic. Apply this policy to the
desired systems but understand that the service, even when set to
automatic, will not start until the next reboot or until the service is
started by a local user, through a remote management console or script,
or through the use of a scheduled or immediate task.
To configure AppLocker settings, perform the following steps:
1. | Log on to a designated Windows Server 2008 R2 administrative server.
|
2. | Open the Group Policy Management Console from the Administrative Tools menu.
|
3. | Add the necessary domains to the GPMC as required.
|
4. | Expand the Domains node to reveal the Group Policy Objects container.
|
5. | Either create a new GPO or edit an existing GPO.
|
6. | After
the GPO is opened for editing in the Group Policy Management Editor,
expand the Computer Configuration node, expand the Policies node, expand
the Windows Settings node, and select the Security Settings node.
|
7. | Expand the Security Settings node and select application control policies.
|
8. | Expand the application control policies node and select AppLocker.
|
9. | In the Settings pane, click on the Configure Rule Enforcement link in the center of the page.
|
10. | In
the AppLocker Properties window, check the three check boxes for
Executable Rules, Windows Installer Rules, and Script Rules, select the
Audit Only option from the pull-down menus, as shown in Figure 4, and click OK to define the rule enforcement properties.
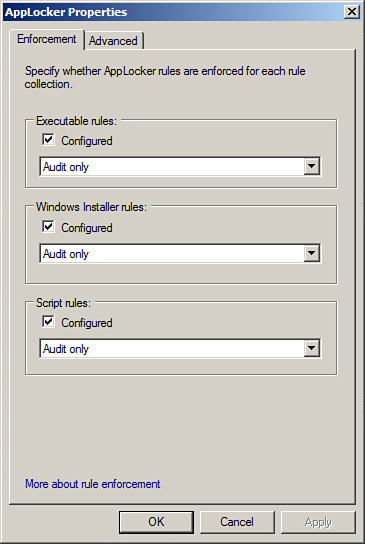
|
11. | Now
before any auditing can be logged, new rules will need to be created.
For this example, right-click on the Executable Rules node beneath
AppLocker and select Create New Rule.
|
12. | On the Permissions page, set the Action to Deny and leave the default group of Everyone, and then click Next to continue.
|
13. | On
the Conditions page, select the Path option button to define a folder
path that will contain executables to which we want to prevent access,
and click Next to continue.
|
14. | On the Path page, type in %ProgramFiles%\* and click Create to define the rule. This defines the c:\Program Files folder as an example.
|
15. | Once
this is completed, save the domain policy and link it to an
organizational unit that contains Windows 7 Enterprise or Ultimate or
Windows Server 2008 R2 systems.
|
16. | Log
on to the desired test system, verify that the new AppLocker policy has
been applied and that the Application Identity service is set to
automatic and is running on the desired machine. Reboot the machine.
|
17. | Log
back on to the test machine and run Internet Explorer or any other
executable that is located beneath the c:\Program Files folder.
|
18. | Now open the Event Viewer console using an elevated account so the audit events can be reviewed.
|
19. | In the Event Viewer window, expand Applications and Services Logs, expand Microsoft, and expand AppLocker.
|
20. | Select the EXE and DLL log and in the Settings pane, verify that warning events are logged, as shown in Figure 5.
If no warning events are logged, the Application Identity service might
not be running and/or a reboot might not have been performed after the
initial AppLocker policy was applied.
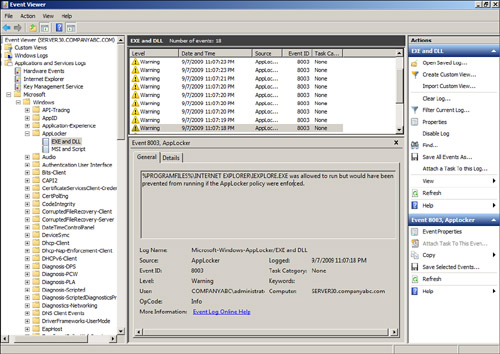
|
21. | Close the event log on the test machine to complete this exercise.
|
AppLocker rules are applied to
the computer object only but unlike software restriction policies,
AppLocker rules applied to a computer can be defined or configured to
apply on a per-user or per-security group basis. Using software
restriction policies, this functionality would apply to all users who
log on to the system based on the enforcement settings. AppLocker will
block all executables, Windows Installer files, and scripts once each of
those rules are enforced. Under each of the rules nodes beneath
AppLocker in the tree pane, policy administrators can use the built-in
function of creating rules based on a wizard and by creating the default
rules. The default executable rules, as an example, once created will
define that everyone can run executables in the Program Files and
Windows folders, including all subfolders, but only administrators can
run executables without path restrictions. To create or populate the
default rules for executables, in the tree pane under AppLocker,
expand AppLocker and right-click on the Executable Rules node and click
Create Default Rules. This generates the three rules described
previously.