Configuring Remote Desktop and Remote Administration Support
A common Group Policy
request from IT administrators who need to support Windows XP, Windows
Server 2003, Windows Vista, Windows 7, Windows Server 2008, and Windows
Server 2008 R2 systems with the Windows Firewall enabled is to allow for
remote administration. Group Policy can manage this task with minimal
configuration. To enable Remote Desktop on Windows XP, Windows 2003,
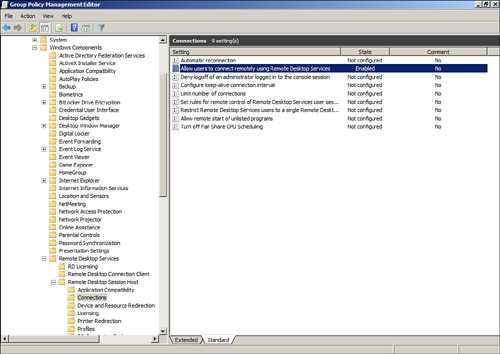
Windows Vista, or Windows Server 2008 systems, enable the Allow Users to
Connect Remotely Using Remote Desktop Services setting. This setting is
located in Computer Configuration\Policies\Administrative
Templates\Windows Components\Remote Desktop Session Host\Connections
node, as shown in Figure 10.
When this GPO is saved and linked to a GPO with computers in it, all
the computers will have Remote Desktop enabled. By default, only members
of the Administrators group will be able to connect using Remote
Desktop. If this needs to be changed, additional users can be added to
the local Remote Desktop Users group.
After
Remote Desktop is enabled on a system, the firewall exceptions still
need to be configured—otherwise, Remote Desktop is not possible. Remote
Desktop is a built-in exception in the Windows XP, Windows Vista,
Windows 7, Windows Server 2003, Windows Server 2008, and Windows Server
2008 R2 basic firewall. In addition, remote administration is a built-in
exception; to configure these exceptions, see the following section, “Configuring Basic Firewall Settings with Group Policy.”
Configuring Basic Firewall Settings with Group Policy
In many organizations,
part of the responsibility of supporting end users requires the ability
to remotely manage the desktop. Many organizations leverage the built-in
Windows tools for remote management, whereas many others utilize
third-party products. Remote management tasks of workstations can
include installing custom software for a particular user or group of
users, manually running Windows Update, assisting with the installation
of local printers, adding local user accounts, changing local group
membership, or troubleshooting reported issues.
The Microsoft Windows
Firewall includes multiple firewall profiles that contain separate
firewall rules and firewall exceptions. Windows XP and Windows Server
2003 contain a domain and standard firewall profile. The domain profile
is activated when the desktop is on the same network as a domain
controller. The standard profile is activated when the desktop is on a
remote or public network, or in many cases, if the machine is connected
to a VPN that does not support proper communication, it might also
remain in the standard firewall profile. Windows Vista, Windows 7,
Windows Server 2008, and Windows Server 2008 R2 contain three firewall
profiles, including the domain profile, the private profile, and the
public profile. The domain profile remains the same, but the previous
standard profile has now been segmented into the private and public
profiles. Any network that is different from the domain network is
initially categorized as an untrusted network and the public firewall
profile is activated. End users, with the appropriate rights, can define
a public network as a private network, which can then activate the
private firewall profile and the appropriate firewall rule set, which is
likely to be less restrictive and might allow the necessary traffic for
the remote client to work correctly on the network they are connected
to. Windows Firewall design and configuration planning is a very
important task for Windows administrators to execute and should not be
taken lightly. Also, disabling firewalls in any profile is not
recommended and is a poor approach to enabling systems and applications
to function on an organization’s network.
To allow Windows
administrators to continue to manage and administer Windows server and
desktop systems remotely, certain firewall exceptions should be defined.
Aside from enabling Remote Desktop, as outlined in the previous
section, remote administrators might need to copy files to and from
systems and utilize Microsoft Management Console snap-ins such as
Windows Server Backup, Event Viewer, Computer Management, and many
others from remote administrative workstations. To enable the Remote
Desktop and Remote Administration exceptions in the Windows Firewall
using domain group policies, perform the following steps:
1. | Log on to a designated Windows Server 2008 R2 administrative server.
|
2. | If necessary, install the Group Policy Management Console on the system.
|
3. | After the tools are installed, click Start, click All Programs, click Administrative Tools, and select Group Policy Management.
|
4. | Add the necessary domains to the GPMC as required.
|
5. | Expand the Domains node to reveal the Group Policy Objects container.
|
6. | Either create a new GPO or edit an existing GPO.
|
7. | After
the GPO is opened for editing in the Group Policy Management Editor,
expand the Computer Configuration node, expand the Policies node, and
select the Administrative Templates.
|
8. | Expand
the Administrative Templates node, expand the Network node, expand the
Network Connections node, and select the Windows Firewall node.
Configurations made in this section apply to Windows XP, Windows Vista,
Windows 7, Windows Server 2003, Windows Server 2008, and Windows Server
2008 R2. However, for more granular firewall configuration for Windows
Vista and later operating systems, the Windows Firewall with Advanced
Security setting can be used.
|
9. | In the tree pane, expand the Windows Firewall node to reveal the Domain Profile node, and select it.
|
10. | In
the Settings pane, locate the setting named Windows Firewall: Allow
Inbound Remote Administration Exception, and double-click on it to open
the setting for editing.
|
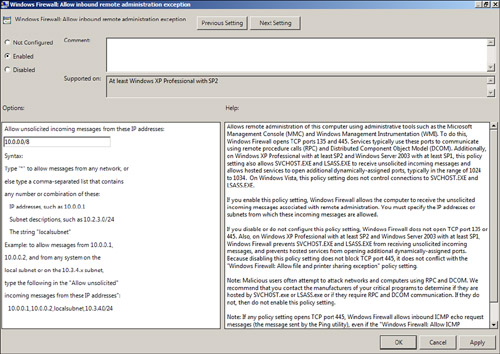
11. | In
the Setting window, click the Enabled option button, and type in the
network from which inbound remote administration will be allowed. For
this example, consider an organization that utilizes the 10.0.0.0
network with a subnet mask of 255.0.0.0. This would be defined as
10.0.0.0/8 in the properties of this exception, as shown in Figure 11. When finished, click OK to update the setting.
|
12. | After
the previous setting has been configured, back in the Settings pane,
select the Windows Firewall: Allow Inbound Remote Desktop Exceptions,
and double-click on it to open the setting for editing.
|
13. | In
the setting window, click the Enabled option button, and type in the
network from which inbound Remote Desktop connections will be allowed.
When finished, click OK to update the setting.
|
14. | If
necessary, repeat the process of configuring the inbound remote
administration and Remote Desktop exception in the standard profile to
ensure that remote management from the defined network will function
regardless of which firewall profile is currently activated on the
client.
Note
If the network defined within a
Windows Firewall exception is a common network, such as 192.168.0.0/24,
the configuration of these exceptions in the standard profile is
considered risky and should not be performed. Instead, work with the
networking group and VPN configurations to ensure that when users
connect remotely to the network from remote sites and through VPN
connections, the system will always recognize and apply the domain
profile.
|
15. | Back
in the GPMC, link the new remote administration firewall exception GPO
to an OU with a computer that can be used to test the policy.
|
16. | After
the testing is completed, configure security filtering and possibly
also WMI filtering to limit the application scope of this policy and
link it to the desired organizational unit(s).
|
Configuring Advanced Firewall Settings
Windows Vista, Windows 7,
Windows Server 2008, and Windows Server 2008 R2 have a new and improved
firewall that enables administrators to define granular inbound and
outbound firewall rules and exceptions in the default firewall profiles.
Even though the Windows Firewall is enabled and active by default on
Windows Server 2008 R2, when the Add Roles Wizard is run and a role,
role service, and/or feature is added to the Windows Server 2008 R2
system, the necessary firewall exceptions are also configured as part of
the process.
This is a major advantage compared with what was included in Windows
Server 2003. However, be aware that when adding additional applications
or services (that are not included with the product) to a Windows Server
2008 system, unless the installation of that product also has a
built-in feature to enable and configure the necessary exceptions in the
firewall, the exceptions will need to be defined and configured
manually. When custom firewall rules, exceptions, and changes to the
default behavior and configuration of the firewall profiles are
required, the settings need to be defined using the Windows Firewall
with Advanced Security console. If these settings need to be defined
using a domain policy, access to these policy settings are included in
the Computer Configuration\Policies\Windows Security\Security
Settings\Windows Firewall with Advanced Security settings node. One
advantage of using Windows Firewall with Advanced Security is that when a
system is configured manually and all of the necessary exceptions and
rules are defined within the firewall, these rules can be exported from
the firewall and imported into a domain policy and applied from the
central location to all of the desired servers.