Understanding Common Security Risks and Threats
In the area of computer
security, it is often wise to know the methods of the “enemy.” That is,
it’s important to understand ways in which malicious programs or people
might be able to perform unwanted actions on your computer. Some of
these actions might include the following:
Using system resources
Malicious programs might use CPU, memory, disk, and network resources
to perform their tasks. In one example, users’ computers are used to
launch an attack on another site or computer without their knowledge. In
those cases, users might notice that their computer appears to be
working more slowly than before.
Tampering with critical system files or data
In some cases, the data might simply be destroyed. In other cases, it
might be transmitted to other computers. Regardless, these changes can
cause data loss and instability of the operating system.
Attempting to obtain personal information such as credit card numbers, user names, and passwords Often, this data is then transmitted to a remote computer, where it might be used for actions such as identity theft.
Tracking system usage
Software that is commonly referred to as spyware often runs in the
background on a computer, unknown to users. It collects information such
as Web sites that are visited and then reports this information back to
the distributor of the software. Apart from violating security, this
can lead to system slowdowns and instability.
Displaying unwanted advertisements
It is a common practice for applications to include additional software
that is installed with little or no warning to the user. The additional
code can perform operations such as automatically loading content from
Web sites.
Some of these programs
might be designed with a specific purpose in mind (for example,
collecting potentially useful personal financial data). In other cases,
the programs might have no purpose other than to annoy the user.
Regardless of the authors’ goals, it’s obvious that malware should be
prevented from running on desktop computers.
Understanding the Security Goals of Windows Vista
A fundamental
principle of managing security is giving users and applications a
minimal set of security permissions. This ensures that they can perform
the most common operations that they need to accomplish tasks, but it
greatly limits the potential damage that a malicious program can cause.
For example, users rarely (if ever) need to modify operating system
files directly. By preventing them from performing this action, the
operating system can avoid the mistaken or malicious deletion of
critical components. By default, applications that a user launches
inherit all of the permissions of that user. If a user can open a
Microsoft Word document, type a letter, and then e-mail it, a program
could easily perform the same actions automatically. Therefore, it’s
important to place restrictions.
Microsoft had two primary
goals when designing security for the Windows Vista operating system.
The first was to ensure that users and applications were granted a
minimal set of permissions for completing common operations. The other
goal, however, was to ensure compatibility with earlier applications. In
previous versions of Windows, it was very common for programs to assume
that they had full access to the computers on which they were running.
They could easily perform tasks such as reading and writing files from
the file system and making modifications to the system registry. Because
developers relied on these capabilities, it was often necessary for
users to log on to their systems with accounts that had full
administrative permissions. If the permissions were not available, the
application might fail to run or might return errors to the user. Based
on the two goals of security and compatibility, let’s look at some new
architectural features in Windows Vista.
|
Anil Desai
There’s no doubt about
it: things would be far simpler for everyone involved if security were
not a concern. In the early days of desktop computing, users and
programs expected to have full control of their computers. Accordingly,
application developers designed their programs under the assumption that
they would also have these permissions and rights. Users would be able
to perform any action they required on their systems. Unfortunately,
having these abilities also increases potential security risks.
|
It is very important
to understand that maintaining complete end-to-end security requires a
team effort. It has been said that a chain is only as strong as its
weakest link. It’s not enough for a few users to follow the rules: all
must do so. Application developers, home and business users, and
Consumer Support Technicians must all exercise discipline to minimize
security issues.
For example, from a
network standpoint, having the world’s most sophisticated and powerful
firewall software won’t prevent users from using their initials as their
password. A malicious user might easily circumvent all of this
protection simply by guessing the password. Similarly, you can easily
disable the many security features in Windows Vista with just a few
mouse clicks.
So how can you, as a
Consumer Support Technician, do your part? Perhaps the most important
aspect of ensuring security for the customers you support is to make
sure that they understand the importance of features such as UAC. Users
often don’t see the benefits of limiting what they can easily do on
their systems. This can lead them to circumvent or disable the features
altogether. When, on the other hand, they see the potential benefits of
security, they are much more likely to use best practices. Overall, it’s
your job to help lead the security team effort.
Understanding the UAC Process
In previous versions of
Windows, it was most common for users to log on to their computers by
using an account that had Administrator permissions. This meant that the
user (and any program that he or she launched) would be able to perform
any operation on the computer. This includes reading and writing to
critical operating system files and accessing data stored anywhere on
the system. In Windows Vista, it is recommended that users log on to the
computer, using a limited set of permissions.
Microsoft designed the
UAC feature of Windows Vista to allow users to log on to their computers
using a standard user account. They can perform the majority of their
tasks using a limited set
of permissions. During the logon process, Windows Explorer (which
provides the user interface for Windows Vista) automatically inherits
the standard level of permissions. Additionally, any programs that are
executed using Windows Explorer (for example, by double-clicking an
application shortcut) also run with the standard set of user
permissions. Many applications, including those that are included with
the Windows Vista operating system itself, are designed to work properly
in this way.
Other applications,
especially those that were not specifically designed with the Windows
Vista security settings in mind, often require additional permissions to
run successfully. These types of programs are referred to as legacy applications.
Additionally, actions such as installing new software, and making
configuration changes to programs such as Windows Firewall, require more
permissions than what is available to a standard user account. Windows
Vista can automatically detect when an application is attempting to use
more than standard user privileges.
Understanding Standard User Mode
When a user logs on
to Windows Vista by using a standard user account, Windows Explorer and
all other processes that are launched run with a minimal set of
permissions. In this mode, UAC requires the user to provide credentials
to the system whenever an application or operation requires elevated
permissions. When an application or process requests access to more
permissions, the user is prompted for approval. This process is known as
application elevation because it allows Windows Vista to give a program
a full set of permissions. Figure 1
shows a sample screen. After the credentials are provided and accepted,
the program runs with elevated permissions. The user, however, still
continues to have only a limited set of permissions.
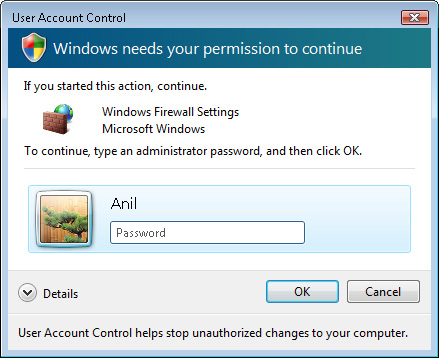
In
a typical consumer environment, the user might already have knowledge
of the user name and password of an Administrator account on the
computer. By providing those details, he or she is implying that he or
she wishes to allow the program to run in an elevated way. Other users
of the computer who do not have these credentials will be unable to
perform administrator-level actions.
Another way in which
the standard user mode can be used is often called the “over the
shoulder” method. In this case, a parent or supervisor might want most
users to run under the standard user mode. Whenever there is a need to
elevate privileges, this person can provide the necessary credentials.
For example, a mother might want her child to log on to the computer as a
standard user. Whenever the child needs to perform tasks such as
changing system settings or installing new software, the mother must
provide the necessary credentials.
Understanding Admin Approval Mode
In some cases, users
might want to log on to the computer by using an Administrator account
but still have the security benefits of running with minimal
permissions. UAC provides this ability by using the Admin Approval Mode.
The user account technically has full permissions on the system, but
UAC limits which actions the user can perform. This effectively makes
the account behave like a standard user account for most operations.
Actions that require additional permissions can be performed, but the
user must first approve them.
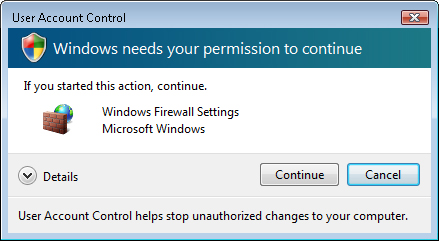
When an
application requests elevated privileges, the default prompt Windows
Vista shows to the user is one that asks the user to provide consent
(see Figure 2).
This method ensures that the user is aware when an application is
attempting to run with elevated privileges. It can also help prevent
situations in which malware applications attempt to modify the system.
However, by default, it does not require the user to provide credentials
for an Administrator account, because the current account already has
this ability. Later in this lesson, you’ll see how you can change UAC
settings to require credentials in Admin Approval Mode.
Additional Security Features
In addition to the UAC elevation prompts
in Windows Vista, there are several other security-related enhancements
that have been designed to increase safety and provide compatibility
for earlier applications. In this section, you’ll learn about how they
work.
File System and Registry Virtualization
Two important areas of
security-related concerns are the Windows file system and the registry.
The file system contains files ranging from operating system components
to user data. In the past, applications were designed with the
assumption that they would be able to access these files and settings
freely. These earlier applications often fail to run properly when they
cannot make those changes.
To prevent direct access
to secure file system locations (such as the operating system and
Program Files folders), Windows Vista uses a technique called
virtualization. This method works by monitoring for when applications
request direct access to the file system or registry. When this occurs,
the operating system automatically redirects the requests to the
appropriate location. For example, if a previous program is attempting
to write a configuration file to the Program Files folder, Windows Vista
automatically intercepts that request and writes the file to a
subfolder of the User profile. This is a much safer operation, and it
still enables the application to run without modifications.
Note: Temporary compatibility measures
Microsoft designed
file system and registry virtualization technology primarily for
compatibility with the vast library of earlier applications that were
written for previous versions of Windows. Over time, many applications
will be designed and updated to use safer models for file and registry
access. Therefore, virtualization is being used as a temporary measure
to bridge the gap until that happens. It is not intended to be used as a
long-term compatibility solution.
Understanding the Secure Desktop
One method by which
malicious applications might attempt to collect sensitive information
from the user is by emulating a standard application or window. This is
particularly true of the UAC elevation prompt. Users might be prompted
for credentials by an unauthorized application that appears to be a
standard Windows dialog box. The program collects user names and
passwords and then might use this information to compromise security.
To prevent this
problem, Windows Vista displays elevation prompts, using a secure
desktop. The secure desktop automatically dims the desktop background
and prevents all applications from launching any new prompts or windows
until the user makes a decision related to the UAC elevation prompt. In
this way, the user can be assured that the UAC prompt is coming from the
Windows Vista operating system itself.
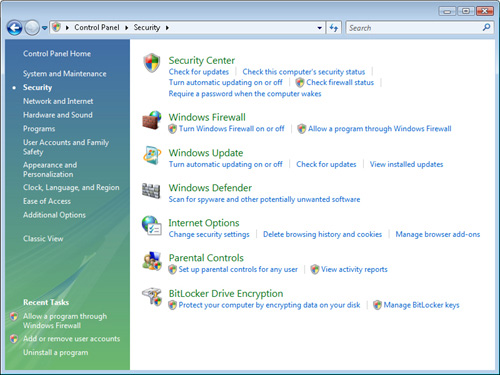
Identifying Tasks That Require Privilege Elevation
Although you can
perform the majority of common tasks in Windows Vista as a standard
user, there are various functions that require elevated privileges.
Built-in operating system tools and applications use a shield icon next
to the appropriate button or link to indicate that privilege elevation
is required (see Figure 3). This helps users understand when they are performing potentially unsafe actions.
Responding to Elevation Prompts
A common source
of security-related and configuration-related issues occurs when users
install unknown applications. In some cases, this might be done
deliberately, but in other cases, users might be tricked into running a
setup program without knowing it. UAC automatically attempts to verify
whether an application is a known program or potentially unsafe. Figure 4 shows an example of the approval dialog box that is presented to users.
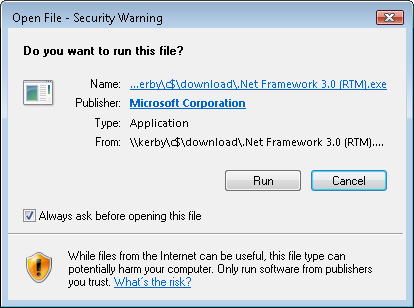
In addition to providing
the name of the program and its publisher (if available), the details
include the full path to the application. This can help users determine
whether they really want to install the program. Options include
allowing or disallowing the program to run.
Running Programs with Elevated Privileges
In some cases, users
always want to run a particular program using Administrator permissions.
For example, a customer might know that her former accounting software
requires elevated permissions, and she does not want a prompt to appear
automatically every time she launches the application. Run This Program
As An Administrator offers the option to run a program always as an
administrator. You can configure this setting on the Compatibility tab
of a program or shortcut (see Figure 5).
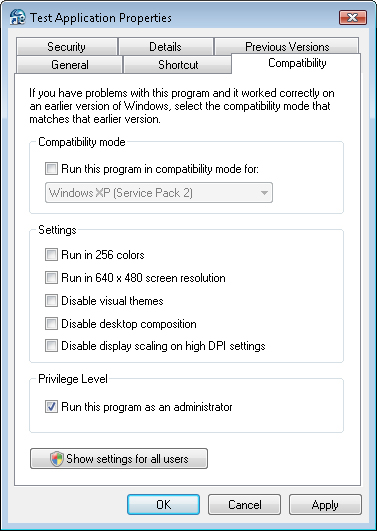
In
some cases, the Run This Program As An Administrator check box might be
disabled. For example, the application might be a built-in program that
is included with Windows Vista and might not require elevated
credentials. In those cases, the check box is disabled.
Another way to launch a
program with elevated permissions is to right-click a program or
shortcut and select Run As Administrator. This setting launches the
application with Administrator permissions. Unless UAC is disabled, the
user is prompted to provide consent or credentials.
Understanding Installer Detection
Perhaps one of the most
common tasks that requires elevated privileges is the process of
installing new software. Setup programs and installers often need to
write directly to secure file system locations (such as the Program
Files folder) and make changes to the registry.
Windows Vista uses
methods to identify installation programs automatically and
automatically prompts for approval of elevation when the application is
run. This helps prevent common error messages and issues that users
encounter when attempting to install programs, using standard user
permissions.
Note: Choosing new applications
Whenever
possible, recommend that customers select software that includes the
Certified for Windows Vista logo. This helps ensure that the product has
been designed for compatibility with UAC and other security features.