Enabling and Disabling UAC
To ensure security of
new Windows Vista installations, the UAC feature is enabled by default.
When users log on to the computer, they start launching processes under
the context of a standard user.
There are several
different ways to control the behavior of the UAC feature. In some
cases, customers might ask you for information about how to disable the
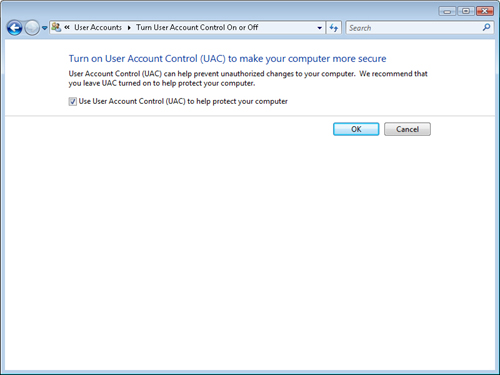
feature altogether. You can access the Use User Account Control (UAC) To
Help Protect Your Computer check box from within Control Panel . This
check box is available by clicking User Accounts And Family Safety and
then clicking User Accounts. You can also access this check box by
searching for UAC in Control Panel. As shown in Figure 6, the dialog box provides a single check box that determines whether UAC is enabled.
Note: Questioning the decision to disable UAC
When
a customer asks how he or she can completely disable UAC, it’s a good
idea to get some more information about why he or she is making this
request. Is the customer frustrated with the frequency of elevation and
consent prompts? Is he or she having difficulty running certain
applications? Often, users don’t understand the value of the UAC feature
and therefore see it as only an annoyance. As a Consumer Support
Technician, explain the purpose and function of UAC, including how it
can help prevent security issues and increase system reliability. It’s
quite likely that customers might decide that disabling the feature
completely is too much of a risk and that changing various settings
might be a much better overall solution. Remember, your goal should be
to strike a balance between security and usability.
After selecting to
enable or disable UAC, you are prompted to reboot your computer, which
is necessary to make the changes effective. When you disable UAC, users
receive a notification of this whenever they log on to the computer or
access security-related settings in Control Panel. This is done to
remind users that they are at risk of potential security issues. You’ll
look at ways in which you can fine-tune the behavior of UAC later in
this lesson.
Managing UAC Settings with Local Security Policy
In addition to the
default behavior of UAC, there are several different options that you
can use to control the specific way in which this feature works. You
define these settings by using policy settings on the computer. To
access them, open the Local Security Policy console from the Start menu.
The utility is available in the Administrative Tools program group (if
the Start menu options are set to display it) or by searching for Local
Security Policy. The default interface shows several different groups of
settings, each of which has dozens of available options.
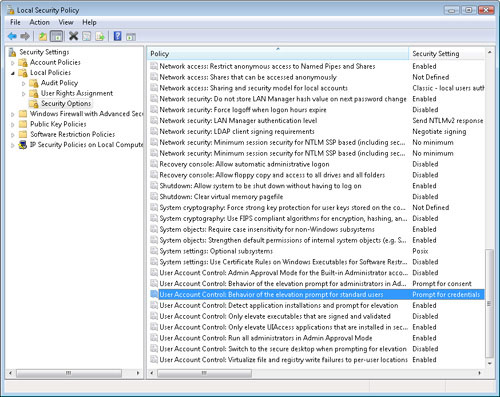
To access the
properties of the UAC functionality, expand Local Policies, and then
select the Security Options folder. The right side of the console shows
all of the available policy options along with their current settings.
UAC-related policies are prefixed by the text User Account Control (see Figure 7).
Each of the settings
pertains to some aspect of system behavior or permissions. For example,
you can use the Accounts: Guest Account Status option to specify whether
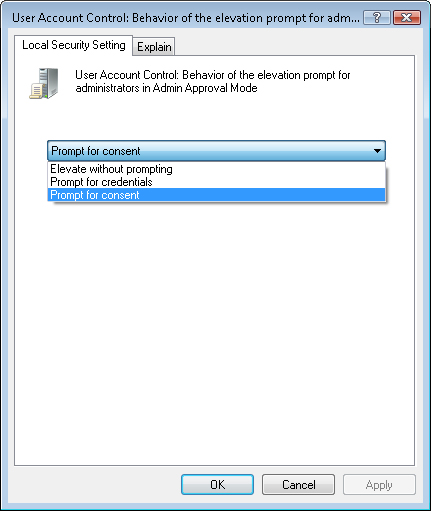
the built-in Guest account is enabled. To make changes to a policy
setting, double-click the item in the list. For most options, the first
tab that is shown, Local Security Setting, provides the options for the
setting (see Figure 8).
It’s often
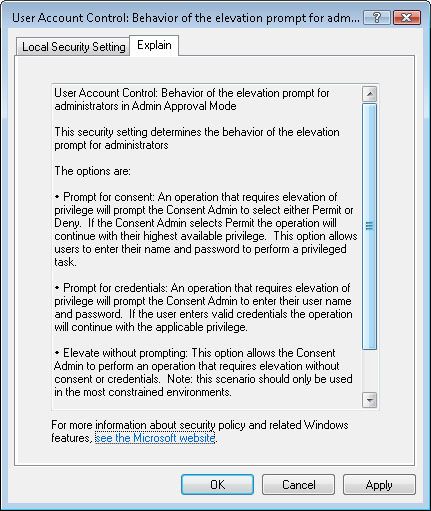
difficult to understand the exact purpose of every available option.
Fortunately, the Local Security Policy console also includes details
about specific options on the Explain tab. The text that is displayed
here (see Figure 9)
provides background information about the policy, along with details
about the effects of these settings. Most explanations also include
details about the default setting for the option. This can be very
helpful in troubleshooting configuration issues. In some cases, links to
more information are provided. Overall, this can help you determine the
purpose and function of each setting.
Note: Resisting the urge to tweak
With
all of the options available in the Local Security Policy console, it
might be tempting to try to change configuration settings just to see
what happens. Although this can be a good method for learning, it’s
important to make these changes on noncritical systems (such as a test
computer). Keep in mind that it is possible to “break” certain
functionality with improper settings.
In relation to
controlling the behavior of UAC, there are nine different settings that
you can configure manually. These are as follows:
User Account Control: Run All Administrators In Admin Approval Mode
This setting can be considered a “master switch” that determines
whether UAC is enabled on the local computer. The default setting is
Enabled. The status of this setting corresponds to the Turn User Account
Control (UAC) On Or Off setting in Control Panel. When the status is
set to Disabled, Admin Approval Mode, file system and registry
virtualization, and all related settings are effectively disabled. It is
important to keep in mind that the other settings might appear to be
properly configured, but they do not have any effect when this setting
is disabled.
Exam Tip
Instead of memorizing
the names of each of the UAC-related Group Policy settings, concentrate
on the meanings and effects of each. On the exam, you’ll be expected to
understand how the settings are used, but you won’t be tested on the
exact wording of each setting.
User Account Control: Admin Approval Mode For The Built-In Administrator Account
This setting specifies the UAC options for the built-in Administrator
account. By default, this setting is set to Disabled, which means that
users who log on with the Administrator account have full permissions on
the system. In general, it is recommended that the default
Administrator account not be used. If you do have a need to enable the
Administrator account, you can add security by enabling this policy
setting.
User Account Control: Behavior Of The Elevation Prompt For Administrators In Admin Approval Mode
This setting specifies the type of elevation prompt that will be
presented to administrative users when a program or process requests
additional privileges. The settings include:
The
default setting provides a balance between security and usability. To
improve security, you can require that administrators provide a user
name and password to elevate permissions. Alternatively, you can choose
to eliminate the prompt altogether.
User Account Control: Behavior Of The Elevation Prompt For Standard Users This
setting determines how elevation prompts will be shown to standard
users. The default setting, Prompt For Credentials, requires the user to
provide logon information for an Administrator user every time an
application or process requests elevated permissions. In some cases, you
might want to prevent elevation from occurring at all. That’s the
purpose of the Automatically Deny Elevation Requests option.
User Account Control: Detect Application Installations And Prompt For Elevation
When users attempt to install an application, Windows Vista
automatically attempts to elevate privileges. This is a useful feature,
because most setup and installation programs require access to the file
system and other protected areas of the computer. The default setting
for consumer-focused editions of Windows Vista is for this option to be
enabled. This means that users automatically see an elevation prompt
whenever they launch an installer. The Disabled option is primarily used
in company network environments in which IT staff can control the
installation of software, using centralized methods.
User Account Control: Only Elevate Executables That Are Signed And Validated
One important potential security risk related to working with
applications and software is in trusting the publisher of the
application. Malware could easily create a new executable or shortcut
that appears to be a familiar application (such as Microsoft Word), but
that actually launches malicious code that could damage the system. One
way to validate a program is to use a method based on Public Key
Infrastructure (PKI) technology. This method allows trusted third
parties to validate whether the publisher of the software is who it
claims to be.
This
option is set to Disabled, by default, because PKI technology has
dependencies on other services such as a Certificate Server. Home and
small-business users are unlikely to have the necessary infrastructure
to do this.
User Account Control: Only Elevate UIAccess Applications That Are Installed In Secure Locations
Some applications might need to run with elevated privileges on Windows
Vista. Developers of these applications can create a setting that
instructs the operating system to prompt for elevated privileges
automatically whenever the program is launched. One potential problem is
for malware (such as programs downloaded from the Internet) to request
full permissions and then make undesired changes to the system. This
setting specifies that only applications that are located within known
secure file system locations (such as the Program Files folder and
subfolders of the Windows folder) are able to request elevation. This
helps ensure that only properly installed programs are able to run with
elevated permissions. The setting can be disabled, although this will
reduce overall security.
User Account Control: Switch To The Secure Desktop When Prompting For Elevation
One method that malware authors have at their disposal is the
possibility of tricking a user into providing sensitive information to a
program. For example, a program could be designed to look very similar
to the standard UAC elevation prompt. A user might provide
a user name and password for privilege escalation, but the application
itself is recording or sending this information elsewhere. To help
prevent this type of intrusion, the default setting in Windows Vista is
to use a secure desktop when an elevation prompt is presented. When this
occurs, the entire desktop background is dimmed, and only the prompt is
shown. Other applications will be unable to overwrite the prompt or
create new windows that take the focus. When you disable this option,
the UAC prompt appears like any other window. However, it is then
possible for other applications to create a false UAC prompt.
User Account Control: Virtualize File And Registry Write Failures To Per-User Locations
This setting is designed to provide compatibility with legacy
applications that request direct access to the file system or to the
registry. When a program attempts to perform one of these actions,
Windows Vista automatically redirects the request to a safe, virtual
location. The benefit is that the program can still run successfully,
but all write operations occur safely. When you disable this setting,
earlier applications are prevented from directly writing to file system
and registry locations. In most cases, this means that the applications
fail to run correctly.
Note: Educating customers
When supporting customers
who are attempting to understand the purpose of various security
settings, you might be tempted just to make various changes on their
behalf. It’s important, however, that you keep the customer informed of
the effects of your modifications. After all, if a security issue or
malware infection were to occur on customers’ systems due to a change
you made, you want to ensure that the user agreed with it. Generally,
the more educated customers are with relation to security, the more
likely they are to exercise good judgment.