Overview of Windows Security Center
Windows Security Center
is an application that is included with all of the consumer-based
editions of Windows Vista. Windows Vista includes numerous
security-related features and settings. To get an overview of the
available options, you can open Control Panel and click Security. Figure 1 shows the default display.
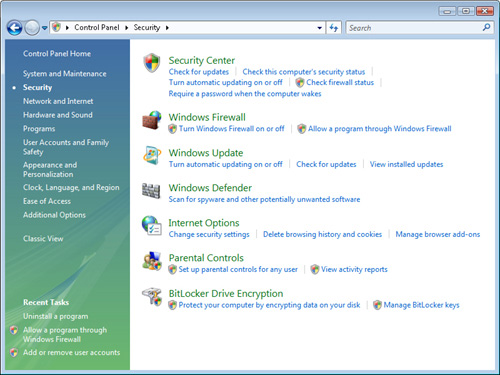
The first available link provides access to Security Center. Figure 2 shows the basic user interface of the Windows Security Center application.
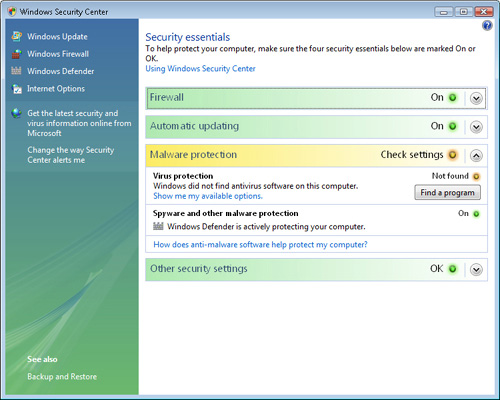
Microsoft
designed Windows Security Center to provide you with an overview of the
various different security configuration features and to provide a
quick method of detecting any potential problems. The default display
provides information related to the following four different types of
security features:
Firewall
Automatic updating
Malware protection
Other security settings
The color of each
section provides you with an overview of the status of each of these
areas. Green indicates the current settings are optimal from a security
standpoint and that this feature or setting is correctly configured
based on recommendations. Yellow indicates that there is a potential
issue with the configuration of current security settings or that the
security level could not be determined. Finally, red indicates that one
or more configuration settings might not be configured according to
security recommendations.
Understanding Security Details
Initially, all of the
Windows Security Center sections are displayed in a collapsed view.
This allows you to get an overview about the overall status of security
easily. However, you can also expand each section by clicking the title
of the item or the arrow on the right side of the bar. When expanded,
each section provides additional details related to the item’s status.
This is especially useful for items that are colored yellow or red,
indicating that there is a potential configuration setting or feature
that could be improperly configured.
Note: Security in previous versions of Windows
Microsoft first
introduced the Security Center feature to the Microsoft Windows platform
in Windows XP Service Pack 2. If you’re supporting users who are
running this version of Windows, you will find several of the features
and settings to be similar to those of Windows Vista. It is still
important to keep in mind that Windows Vista includes numerous features
and additions that make it more secure than earlier versions of the
Windows platform.
Changing Windows Security Alerts Settings
In cases in which
the configuration of security-related applications and settings is not
set based on recommendations, Windows Vista can automatically alert
users about the issue by displaying an icon or notification in the
system tray. The icon, called Windows Security Alerts,
provides a shield icon with explanatory text about the issue. You can
configure the exact behavior of Windows Security Alerts by clicking
Change The Way Security Center Alerts Me in Windows Security Center. Figure 3 shows the available options.
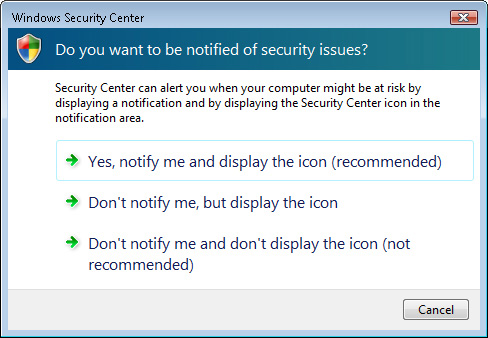
The options include the following:
Yes, Notify Me And Display The Icon (Recommended)
Don’t Notify Me, But Display The Icon
Don’t Notify Me And Don’t Display The Icon (Not Recommended)
The default and
recommended option is to display the notification and the icon. This
setting is useful because it helps ensure that users are notified
whenever there is a problem related to configuration settings. If users
want more information about the problem, they can click the
notification. They can also launch Windows Security Center by
right-clicking the shield icon in the system tray and then choosing
Security Center from the shortcut menu. These features ensure that users
are aware of their security status even when they do not manually open
Windows Security Center.
Now that you have a basic idea of the purpose of Windows Security Center, you’ll look at each of the major areas in more detail.
Configuring Windows Firewall
From a usability
standpoint, it’s often helpful to enable computers to communicate with
each other without any restrictions. If you can trust all of the
computers and users in the environment, this will allow for the easy
flow of information. In many environments, however, security risks
require limited network connectivity. The goal is to enable authorized
communications and keep unwanted network traffic out.
A firewall is designed
to provide a logical layer of protection between computers in a
networked environment. For example, home users might want their home
computers to communicate with each other but want to prevent users on
the Internet from accessing their computers
directly. Microsoft designed Windows Firewall to restrict inbound and
outbound traffic based on a series of configurable rules. The goal is to
ensure that only certain types of applications and services are able to
connect to the computers.
Understanding Inbound Filtering
Filtering
inbound traffic can be very useful in preventing many kinds of common
network-based attacks. Especially when computers are directly connected
to the Internet, it’s common for other computers and malicious users to
scan for computers that are not properly protected and try to access
them.
For example, if
an application such as a Web server can be directly accessed from
another computer, it’s possible for malicious users to exploit known
vulnerabilities in the product to gain access to the system. A firewall
can prevent inbound access to the Web server at the network layer,
thereby avoiding these potential problems. It does this by blocking all
traffic that is inbound to the computer. In some cases, applications or
services might need to access the computer for legitimate purposes. In
these cases, you can create exceptions for known applications.
Understanding Outbound Filtering
Outbound filtering
limits network access for applications and services that are running on
the local computer. For security reasons, not all outbound Internet
access should be allowed. A common method of compromising security is to
have unwanted applications connect to the Internet or to other
computers. In some cases, these applications might be used to download
unwanted advertisements and directly display them on the screen. More
serious problems include collecting data and password information from
the local computer and transmitting it to another computer on the
Internet.
In some cases,
outbound access is required. For example, applications such as Web
browsers and antivirus scanners might need to connect to the Internet
regularly to obtain data. Features of Windows Vista can benefit greatly from having access to the
Internet. The standard approach to meeting these requirements is to
provide a list of exceptions in the outbound firewall configuration.
These settings define which applications and services are able to
communicate across the firewall.
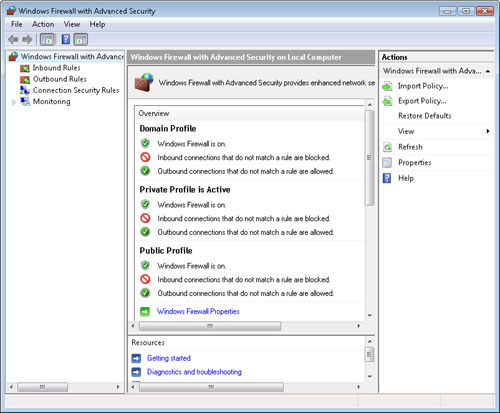
Managing Firewall Settings
There are two
main management methods for the configuration of Windows Firewall. You
can find both by opening Firewall from the Start menu or by accessing
Security in Control Panel and then clicking Windows Firewall. The
default Windows Firewall window shows a simplified display of overall
firewall settings. It provides details related to the current status of
Windows Firewall (see Figure 4).

Users can click
Change Settings to make modifications to the current configuration of
Windows Firewall. The General tab of the Windows Firewall dialog box
(shown in Figure 5) provides a master setting that determines whether the firewall is enabled.
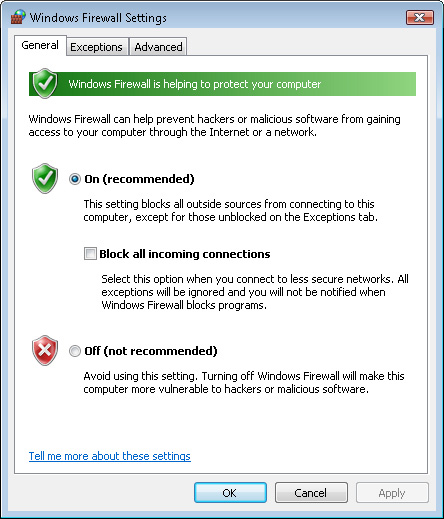
It is strongly recommended
that you configure the firewall to On. When you choose this option, the
Block All Incoming Connections check box is available. Selecting this
check box prevents other computers from accessing any resources on the
local computer, regardless of the configuration settings in other tools
and applications. Therefore, this option is most useful when running in
insecure environments such as a public network.
Users who want to be able to
set up a home network to share media and other files will likely want
to leave the check box cleared. The last option is to disable Windows
Firewall completely. In most cases, use this setting only for temporary
troubleshooting because disabling the firewall can leave the system open
to numerous types of network attacks.
The Exceptions tab
includes a list of all of the different types of applications that are
allowed to communicate through Windows Firewall (see Figure 6).
Because many network-enabled and Internet-enabled applications require
this access, users can specify which applications are allowed to
connect. By default, the Windows Firewall list includes a default set of
allowed outbound connection options. These settings allow commonly used
applications to communicate with other networks.
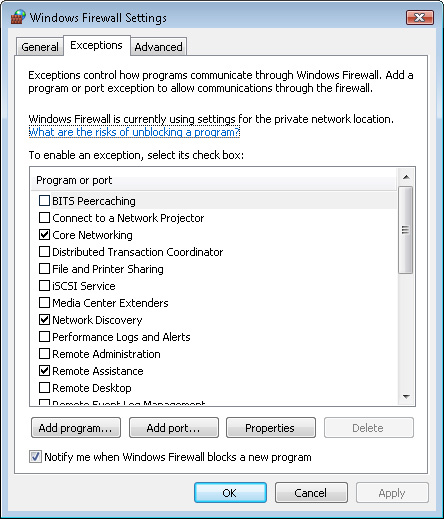
When you install
new applications or enable new operating system features, Windows Vista
might prompt you to approve automatic changes to the firewall
configuration. Regardless of your choice, you’ll be able see which
programs are able to access remote networks, such as the Internet, by
using the Exceptions tab. By limiting the list to only known
applications, you can prevent malware and other programs from
automatically connecting to the Internet or to other computers.
Finally, the
Advanced tab enables users to configure which network connections use
the Windows Firewall. In most cases, it’s best to leave the firewall
settings on for all connections. In some cases, however, it might be
necessary to disable Windows Firewall. For example, some users might
connect to their work networks from home. If their work network already
has adequate security software and settings, it might be preferable to
turn off the firewall for that particular connection.
The primary goal of the
basic Windows Firewall tool is to provide a quick and easy way for users
to modify the most common settings. The Windows Vista firewall also has
many additional features and functions that you can use to manage
better which types of connections are permitted. You can access these
additional settings by launching the Windows Firewall With Advanced Security console. (You can launch this console from the Start menu or through Administrative Tools). Figure 7
shows the default types of settings that are available.