Troubleshooting Internet Explorer
Although the Internet
provides numerous benefits to computer users, it also provides a method
for malware authors to distribute and collect information from users’
computers. A common target of malware is the Web browser. To protect
against common attempts to install malicious software on customers’
computers, the Windows Vista Internet Explorer 7 Web browser contains
numerous security features.
Malware that targets Web browsers is often designed to make configuration changes. Examples include the following:
Changes to existing bookmarks or the addition of new ones
Automatically redirecting users to other Web sites
Changing security levels for specific sites
Automatically downloading and installing adware, spyware, or other unwanted software
Installation of Browser Helper Objects
Accessing operating system files and user data
Collecting sensitive personal information such as logons, passwords, and credit card numbers
Creating or adding new toolbars
Tracking users’ browser behavior
Features included in
Internet Explorer 7 have been designed to prevent many of these types of
unwanted changes. However, to maintain compatibility with advanced
Web-based user features, it is possible for users to agree unknowingly
to install potentially malicious software. For example, the browser’s
home page might be changed, or the user might start receiving an
extremely large number of pop-up ads.
Deleting Browser History
When
troubleshooting the installation of malware, there are ways to remove or
undo unwanted changes. A quick and easy first step in troubleshooting
browser-related issues can be to use the Delete Browsing History command
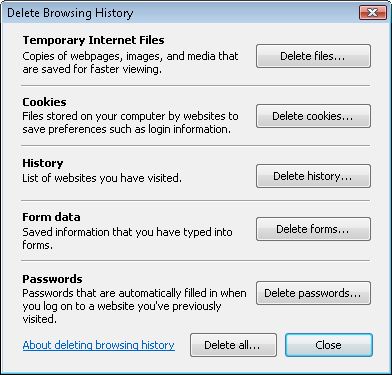
on the Tools menu. As shown in Figure 10, this option enables you to remove files such as cookies that have been stored on the computer.
Managing Add-Ons
Another option for
managing unwanted programs is to view and verify the list of browser
add-ons that have been installed on the computer. Software vendors
create legitimate add-ons to improve the browsing experience. They might
add useful features and functionality to the browser or, perhaps, tasks
that can make working with Web sites easier. Unfortunately, malware
authors can misuse the same features to present advertisements or make
changes to browsing behavior.
To
obtain a list of add-ons that are installed in Internet Explorer 7,
click the Tools menu, select Manage Add-Ons, and then select Enable Or
Disable Add-Ons. Figure 11 shows the Manage Add-Ons dialog box.
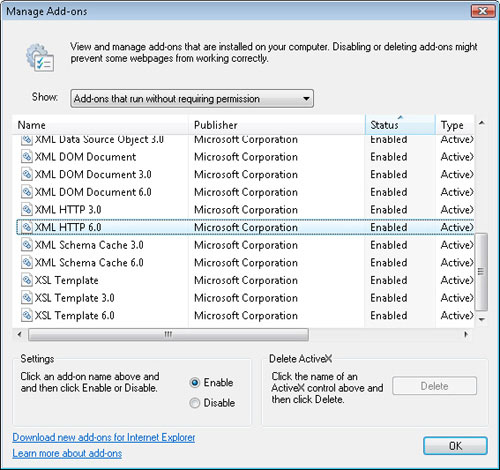
There are four main options in the Show drop-down list that specify which items are shown, as follows:
Add-Ons That Have Been Used By Internet Explorer
Add-Ons Currently Loaded In Internet Explorer
Add-Ons That Run Without Requiring Permission
Downloaded ActiveX Controls (32-Bit)
As a Consumer Support
Technician, you should examine the list of items to identify potential
malware. This can be difficult, however, because the names of some items
might be missing, incomplete, or confusing. The Manage Add-Ons dialog
box also provides the ability to enable and disable the listed items.
Disabled items are prevented from running, but they can also be easily
reenabled in the future. The Delete button in the Delete ActiveX section
provides a way to remove controls permanently that have been downloaded
to the system.
Resetting Internet Explorer Options
In some
cases, you might find that standard troubleshooting steps are unable to
resolve the problems that a user is experiencing. An example might
include the installation of malware that caused numerous changes to
search settings, the default home page, add-ons, and other configuration
details. Alternatively, users might have made numerous changes to their
security settings, and it is difficult and time-consuming to change
them back. For those situations, Internet Explorer 7 includes a feature
that enables you to reset all of the browser settings to their default
values.
To reset the
Internet Explorer settings, click Internet Options in the Tools menu of
the browser. Click the Advanced tab. In addition to a long list of
advanced options, the bottom of the dialog box offers a Reset button.
When you click this button, a message box outlines the changes that
occur if you start the process (see Figure 12).
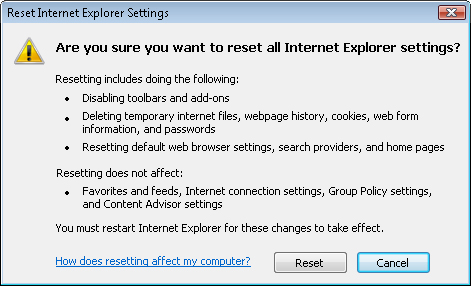
As the warning
message notes, this option is designed for use when other standard
troubleshooting methods have failed. The primary reason for this is that
users might have made numerous useful changes to their browser
settings, and some of those revert to their original values. However, in
some cases, performing a reset of all of the settings might be the
quickest and easiest method of restoring proper operations.
Note: Modifying customers’ computers
As a Consumer
Support Technician, customers trust you to detect and resolve problems
that are preventing their systems from running correctly. They should
also be able to assume that you will not make changes without their
permission. When performing operations that could result in an
inconvenience to the user, always attempt to explain the situation and
obtain his or her approval first. This way, you can verify that it’s a
team decision.
Other Methods of Removing Malware
So far in this lesson,
you’ve looked at ways in which you can use features of Windows Defender
and Internet Explorer to resolve malware issues. In addition to these
tools, there are some other ways in which you can combat malicious
software. In this section, you’ll learn about these methods.
Uninstalling Programs
Sometimes,
the most obvious solutions are the ones technical professionals look to
last. When troubleshooting malware, consider accessing the Uninstall a
Program item in Control Panel. The display returns a list of installed
programs and provides the ability to remove unwanted applications.
It’s unlikely that the author
of a malicious program went through the effort to design a proper
installer and removal utility. However, many pieces of software that
might be considered adware or spyware by some users are designed to
remove themselves properly. For example, if an Internet-based freeware
download included unwanted software, the uninstall process might provide
the option to remove it. Although attempting to uninstall programs
won’t solve all malware-related issues, it does provide a simple way to
remove some of them.
Reinstalling Windows Vista
Although this situation
should be exceedingly rare, there might be cases in which you choose to
reinstall the Windows Vista operating system completely. For example,
some business environments might find that it is too time-consuming to
perform in-depth troubleshooting. Some small businesses might not have
the expertise required to clean malware from computers. In these cases,
the organization might opt to perform a reinstallation of Windows Vista.
Caution: Choosing to reinstall
In most cases,
consider choosing to reinstall the entire operating system due to a
malware problem a last resort. Apart from losing configuration settings,
users might have to spend a significant amount of time reinstalling and
customizing their applications. In some cases, this potential solution
might be worse than the problem. Always try to use all of the other
troubleshooting methods at your disposal before deciding to reinstall
Windows Vista.
An alternative to
performing a full reinstallation is to use other standard diagnostic and
troubleshooting tools. For example, you can attempt to boot the
computer to Safe Mode to prevent unnecessary startup programs from
running.
Keeping up with Security Details
Although you might not
like their products, malware writers do often spend significant amounts
of time coming up with ingenious ways of installing software on users’
computers. Consumer Support Technicians can provide a valuable service
to their customers by remaining up to date on the latest security
issues. A useful starting point is the Microsoft Security At Home Web
site, which is available at http://www.microsoft.com/athome/security/spyware/software/isv/default.mspx. Additionally, numerous third-party vendors and independent security researchers on the Internet keep computer users up to date on potential fraudulent activities.