When managing volume license activation of
Windows Vista, you must choose to use Multiple Activation Key (MAK)
activation, Key Management Services (KMS)–based activation, or a
combination of both, whichever best meets your needs. To select an
activation method, you first need to understand how each works.
1. Centralizing activation with KMS
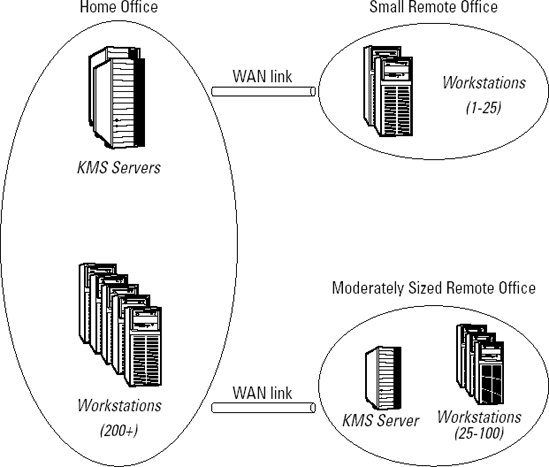
The default activation method for volume license
editions of Windows Vista is to use KMS. KMS is an organizational,
centralized activation solution. The focus of KMS activation is to have a
local server at your organization to activate the Windows Vista
clients, as shown in Figure 1.
The major advantage is that you only need to activate the KMS server
itself with Microsoft, and after you activate your KMS server, no
further communication with Microsoft is necessary to activate your Vista
clients. In fact, you won't have to keep up activation counts either,
because a KMS server will activate as many computers as many times as
you want. Of course, proper licensing needs to be observed to remain
legal, but activation should be much more manageable.
KMS volume activation works in two stages. In
the first stage, you manually configure and activate a centralized
server running the software licensing service. The software licensing
service is included with Windows Vista and Server 2008 and is available
as a download for Server 2003. You begin by changing the product key for
the KMS server to the KMS key provided by Microsoft when purchasing
volume licenses. Each key may activate up to six servers ten times each
without having to call Microsoft for a manual exception. After the
product key has been changed, the server must be activated either
through the Internet or manually by calling Microsoft and entering the
activation code by hand.
NOTE
Although Vista can host a KMS server, it
can only activate other Windows Vista systems. If you need to activate
Windows Server 2008 systems, you will need to host the KMS server on a
Windows Server system. Further, a KMS key can be used to install up to
six KMS host systems (if more are needed, requests can be made to
Microsoft's Volume Activation Support Center).
Just as the new KMS key installed on the server
dictates it will operate as a KMS server, there are KMS client keys that
indicate a workstation or server should activate with a KMS server
rather than against Microsoft activation servers. This key is referred
to as the generic key and is included on the installation media in a
file named pid.txt. To use this key, simply omit a product key when
installing Windows and it will use the generic key and in turn attempt
to activate with a KMS server. However, on which KMS server?
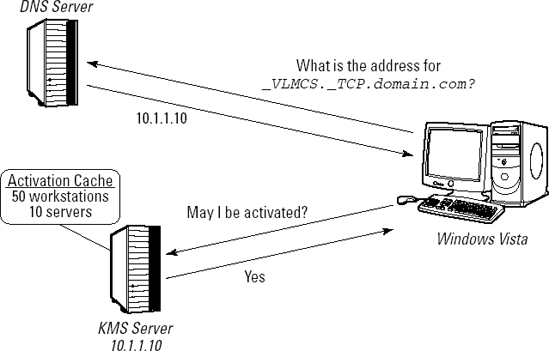
KMS server location
KMS servers are located by clients in one of two
methods. The default and preferred method is to use DNS. When
installing a KMS server key, the software licensing service will
automatically attempt to register itself with its DNS server. If you are
not using dynamic DNS, then you must manually create a DNS entry for
the KMS service. When a KMS client requires activation, it performs a
DNS query to locate a valid KMS server, as shown in Figure 2. Multiple KMS servers may be used and specified in DNS to provide fault tolerance.
|
Although a KMS server will automatically
register itself in DNS, it will not remove itself from DNS when retired.
If you retire a KMS server or simply plan to move the KMS functionality
to another server, be sure to remove the DNS entries manually for the
KMS service referencing the server to be retired.
|
|
Second, clients can locate a KMS server by
manual configuration. If DNS location of KMS servers is not feasible,
then each client may be manually configured to access a KMS server. When
manually specifying a KMS server, there is no fault tolerance.
Therefore, we strongly recommend that you do not employ this manual
configuration unless no other options are available. If manual
configuration is necessary, you can use the slmgr.vbs script and its skms
argument. This command line can be
deployed as a simple task using a desktop management solution (such as
Microsoft System Center Configuration Manager, Altiris Deployment
Solution, or the KBOX Systems Management Appliance), or you can run this
command as a startup script assigned through Group Policy.
Reviewing the limitations of KMS
Although KMS offers a relatively
maintenance-free activation solution, it does have some shortcomings and
limitations. Specifically, you must have a minimum number of systems
requesting activations in order for it to succeed (activation
threshold). You must also configure DNS manually if you have multiple
domains or multiple KMS servers. Clients need to reactivate on a regular
basis. Some OEM systems can have issues with upgrade verification
functions. In this section, each of these issues will be discussed.
Activation threshold
DNS configuration
Reactivation
Upgrade verification
Understanding activation threshold requirements
The most notable is the activation threshold.
The activation threshold is the minimum number of physical computers on
a network that must request activation before activation will occur.
The threshold for Server 2008 is five activation requests; for Windows
Vista it is 25 activation requests. The intent is to ensure that KMS
activation is only used in medium to large businesses, where proper
licensing is more likely to be observed.
When the first computer requests activation from
the KMS server, it responds with a count of one. The second is provided
a count of two. When the fifth computer makes its request, it will
succeed if that computer is Windows Server 2008; if that fifth computer
is Windows Vista, it would not because its activation threshold is 25.
NOTE
KMS can activate both physical and virtual computers, once the threshold of physical computers is met.
Understanding DNS requirements
Another thing you may need to watch out for in
the current KMS implementation is the location of the required DNS
entry. The entry in DNS for a KMS activation server is an SRV record in _VLMCS._TCP.yourdomain.com.
Using this particular location in DNS poses two problems. One problem
is that KMS entries are not site specific and may result in activations
being performed across WAN links, even when a local KMS server is
available. One possible solution is to use separate DNS domains for each
physical location, each with its own list of available KMS servers.
Another problem is that the DNS entry is only
automatically registered in the domain to which the KMS server is a
member. If you are working in a multiple domain environment, you will
need to create an SRV record underneath _VLMCS._TCP manually for each
domain you would like the KMS server to service.
Understanding reactivation requirements
Another limitation, or feature, of KMS is the
need for client reactivation. When activated using KMS servers, clients
are only activated for 180 days and require reactivation to continue to
be used. Under normal circumstances, the clients should manage the
reactivations in the background without any administrative overhead.
Until activated, clients will attempt to activate every two hours. After
activated, clients attempt to reactivate every 7 days, which means that
on a properly operating network with healthy clients and servers,
workstations should always have at least 173 days of activation
remaining.
This works well for environments where
workstations are typically connected to the network. It even works well
with portable computers as long as they connect to the network every few
months. Remote locations that connect to the central office through VPN
even work well with KMS activation and can help meet the activation
threshold. What do not work well with KMS activation are portable
computers that connect to the organizational network infrequently. For
those, you might prefer to use MAKs as described in the next section.
Understanding upgrade verification functionality
Another less common issue associated
with KMS activation is its upgrade verification functionality. As all
volume licenses are upgrades, KMS activation will minimally attempt to
verify that OEM computers were sold with Windows licenses. If the BIOS
of a workstation contains a software licensing (SLIC) table, it must
also contain a Windows marker in that table. This presumably means that
the computer was sold with a valid Windows OEM license and that the
volume license, which is an upgrade, is valid and should be activated.
If your BIOS has an SLIC table but no Windows marker, activation against
a KMS server will fail. The solution would be to use another activation
technique or have your vendor correct the issue.