The bedrock of security in Internet Explorer 8 is its
consistent use of Windows permissions to limit what webpages and
add-ons can do. This security fence around the browser window is called Protected Mode. In the following sections, among other things, we explain how Protected
Mode defangs potentially dangerous add-ons by restricting their access
to system files and redirecting files they save or create to locked-down
virtualized locations. We also explain how Internet Explorer's use of
security zones lets you apply different levels of security to different
categories of sites.
1. Working with Protected Mode
Using a web browser
exposes you to special security risks; by clicking a link in an e-mail
or mistyping a web address, you can find yourself on a site containing
hostile script or downloadable code intended to take over your system.
To mitigate these threats, Internet Explorer runs in Protected
Mode. This special mode, which is active in all Internet Explorer
security zones except the Trusted Sites zone, takes advantage of a wide
range of security-related features, notably User Account Control (UAC).
When Protected
Mode is enabled (the default setting), Internet Explorer runs with
severely limited privileges. These restrictions prevent a website from
installing programs without your permission or changing system settings.
In Windows 7, processes run with integrity levels defined by the Mandatory Integrity Control feature. Protected Mode Internet Explorer runs in the Low privilege process. As a result, Internet Explorer is prevented from writing to areas of the file system or the registry
that require a higher privilege. The information sent between processes
of different integrity levels is also limited with Protected Mode.
Add-ons such as ActiveX controls and toolbars run in the same Low
process, preventing them from gaining access to any areas except those
specifically created for storing potentially unsafe data and programs.
Behind the scenes,
Windows creates a set of folders and files for use with Protected Mode
Internet Explorer. These folders and files share the same Low privilege
level as Internet Explorer. Windows also creates virtual
folders to store files that Internet Explorer tries to save in
protected locations. Instead of causing an add-on to fail when it tries
to write a data file to the Program Files or Windows folders, Windows
silently redirects the file write operation to a virtual equivalent. The
program is able to continue, believing that it wrote the files to a
system location and not realizing that the data files actually wound up
in a hidden vir-tualized folder that mirrors the actual path and is
stored under the Temporary Internet Files folder. Likewise, any attempt
to write to the registry is redirected to a Low-integrity area of the
registry.
When Internet Explorer
needs to read those virtualized files, a broker process intercepts the
operation and asks for your consent before continuing. This represents
an important concept of Protected Mode: whenever any action requires a
higher privilege level, such as an ActiveX installation or an attempt to
save a file, a broker process must be invoked.
On rare occasions,
Protected Mode can prevent an application or website from working
properly. If all attempts to work around the incompatibility fail, you
can disable Protected Mode for the current zone. We recommend against
taking this measure; if you must do so, we recommend that you re-enable Protected Mode immediately after you finish the activity that conflicts with it. Follow these steps to disable Protected Mode for the current zone:
From within Internet Explorer, click Tools, and then click Internet Options.
Click the Security tab, and clear the Enable Protected Mode check box.
Click
OK to continue, and close the Internet Options dialog box. Windows
displays a warning that the current security settings will put your
computer at risk. Click OK to continue.
When Protected Mode is off, navigating to any webpage displays a warning message in the Information bar:

To re-enable
Protected Mode, click the Information bar and click Open Security
Settings. Select the Enable Protected Mode check box, click OK, and then
close and reopen Internet Explorer.
Another method
for working around Protected Mode for a specific website is to add the
website to the Trusted Sites zone, where Protected Mode is not in
effect. We recommend that you exercise caution before choosing this
technique, however; adding a site to the Trusted Sites zone enables a
wide range of potentially risky behaviors, and it's easy to forget to remove the site from the Trusted Sites zone after you finish working with it.
2. Using and Customizing Internet Security Zones
Internet Explorer's
security zones are key elements to browsing the web and using the
internet without fear. By default, all websites you visit are assigned
to the Internet zone, and Internet Explorer severely restricts the
action of sites in the Internet zone. If you're concerned about
security, you can lock down security zones even more tightly if you
like.
By default, Internet Explorer allows you to work with four security zones:
The Internet zone includes all sites that are not included in any other category.
The
Local Intranet zone is for sites on your local network—typically,
behind a firewall. Protected Mode is turned off by default in this zone.
The
Trusted Sites zone allows you to specify sites where you allow certain
actions—such as running ActiveX controls or scripts—that you might not
permit on other sites in which you have a lower degree of trust.
Protected Mode is off by default in this zone.
The
Restricted Sites zone allows you to specify sites where you want to
specifically disallow actions that might otherwise be permitted.
2.1. How Security Zones Affect the Way You Browse
When you open a webpage
using Internet Explorer, Windows checks to see which security zone that
page is assigned to and then applies restrictions to that page, based
on the settings for that zone. Initially, any sites you connect to
internally (that is, your own company's sites, which you access by means
of an intranet connection) are automatically assigned to the Local
Intranet zone, and if you choose to enable intranet settings the Local
Intranet zone is accorded a Medium-Low level of security settings. All other sites on the internet are lumped into the Internet zone, which is given a Medium-High
security level. As you roam the internet, if you come upon a site that
you trust completely, you can move that site into the Trusted Sites
zone. Internet Explorer, by default, applies a Medium
level of security settings to the Trusted Sites zone. When you discover
a site that warrants a high degree of wariness, you can move that site
into the Restricted Sites zone. The security settings that apply there,
by default, are described as High.
2.2. Adding Sites to a Zone
To change the zone in
which a site resides or to reconfigure the security settings associated
with a zone, you use the Security tab of the Internet Options dialog box
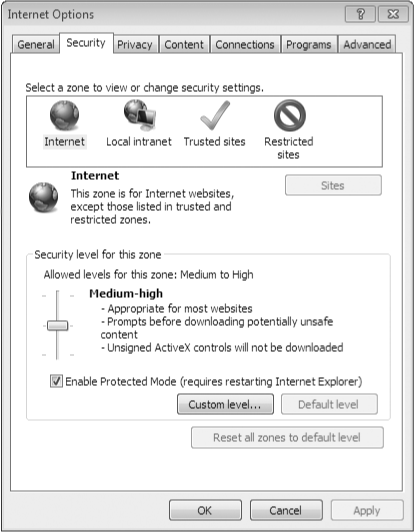
(click Tools, Internet Options, and then click the Security tab), which
is shown in Figure 1.
To add a site to your Trusted Sites or Restricted Sites zone, follow these steps:
On the Security tab of the Internet Options dialog box (shown in Figure 6-16), select Trusted Sites or Restricted Sites.
Click Sites. You'll see the following dialog box (or one similar if you selected Restricted Sites):
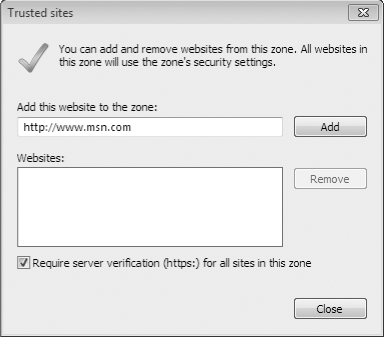
The
URL for the current site appears in the Add This Website To The Zone
box. Edit or replace this value if necessary and then click Add.
By design, the Trusted Sites zone is most appropriate
for use with secure sites, where you already have a high degree of
confidence that the site you're interacting with is legitimate. Thus,
the default
settings for this zone require that Internet Explorer verify that the
site's server is secure (in other words, that its URL begins with https:) before establishing a connection. To add a non–Secure Sockets Layer (SSL) site to the list, clear the check box at the bottom of the Trusted Sites dialog box. (After adding the site, you can select the check box again.) When you add a domain (such as http://www.microsoft.com) to either of these zones, all URLs located within that domain are assigned to the zone you selected.
By default, Internet Explorer populates the Local Intranet zone with the following:
All intranet sites that you haven't moved into either the Trusted Sites zone or the Restricted Sites zone
All sites that bypass your proxy server, if one exists on your network
All network servers accessed via UNC paths (\\server_name)
To remove one or more of
those categories (so that the affected category joins the Internet
zone), select Local Intranet in the Internet Options dialog box and then click Sites. You'll see the following dialog box. Clear the appropriate check boxes.
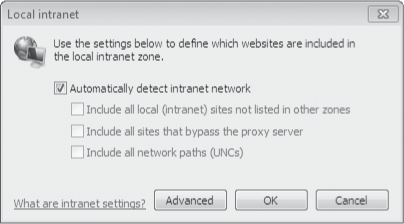
If you want to add a site to the Local Intranet zone, click the Advanced button. Then type the site's URL and click Add.
2.3. Changing a Zone's Security Settings
Any site placed in a
security zone is subject to the same privileges and restrictions as all
other sites in that zone. Thus, if you change the overall security
settings associated with the zone, you change the security settings for
all of its member sites. You can change the security settings for a zone
to one of the predefined groups by following these steps:
On the Security tab of the Internet Options dialog box (shown earlier in Figure 6-16), click the icon for the zone you want to adjust.
Warning:
If you've
previously made any customizations to security settings for a particular
zone, those settings will be wiped out as soon as you click Default
Level. If you've made specific changes to allow a program or site to
work correctly, be sure you document those settings so that you can
reapply them after changing other security settings.
In
the Security Level For This Zone section of the dialog box, click the
Default Level button to reveal a slider control (if the slider isn't
already visible).
Move
the slider up to apply more stringent security measures or down to be
more lenient. As you move the slider from level to level, the
description to the right of the slider summarizes the current level's
settings.
To fine-tune the settings
for a zone or to read all the particulars about the current level of
settings, click Custom Level. In the Security Settings dialog box that
appears, you can use the option buttons to adjust individual settings.
If you've customized
a security zone's settings and you want to start over from a clean
slate, open the Security Settings dialog box, choose a predefined level
from the Reset To dropdown list, and then click Reset.