Files and folders contain data. That data may be
innocuous data that you use regularly and that requires little or no
protection, or it might be critically sensitive data requiring extensive
protection. In each case, you will need to implement a strategy to
protect your sensitive data. A strategy for protecting data will include
but not be limited to a structured design for permissions, storage,
encryption, and auditing.
1. Configure the Encrypting File System
The Encrypting File System
(EFS) is a feature of Windows that you can use to encrypt files and
folders on your hard drive to provide a secure format of storage. EFS is
a core file encryption technology used only on NTFS volumes. An
encrypted file cannot be used unless the user has access to the keys
required to decrypt the file. The files do not have to be manually
encrypted or decrypted each time you use them. They will open and close
just like any other file. Once EFS is enabled, the encryption is
transparent to the user.
Using EFS is similar to using
permissions on NTFS files or folders. However, a user who gets physical
access to encrypted files would still be unable to read them because
they are stored in an encrypted form.
You can encrypt or
decrypt files or folders by setting the encryption property attribute
for the file or folder. The encryption property is an attribute that is
applied much like the attributes of read-only, compressed, or hidden
files or folders, as shown in Figure 1.
To encrypt a file or folder, follow these steps:
Select the file or folder you want to encrypt.
Right-click the file or folder.
Click the Advanced button.
Select the Encrypt Contents To Secure Data box.
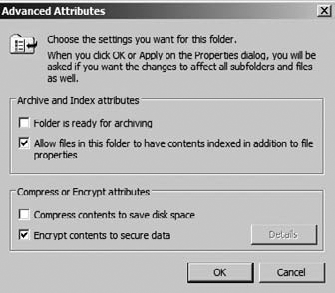
It is important to note
that the attributes of compression and encryption are mutually exclusive
of one another. You cannot do both. If you have a file that is
compressed and you decide you want to encrypt it, you must remove the
compression bit before the file can be encrypted, and vice versa.
The following are some additional considerations when using EFS:
Only files and
folders on NTFS volumes can be encrypted. You can use Web Distributed
Authoring and Versioning (WebDAV), which also works in NTFS volumes to
transfer encrypted files and folders in their encrypted form.
Encrypted files and folders are decrypted if you move them to a volume that is not NTFS.
Moving
unencrypted files or folders into a folder that has been encrypted will
result in the encryption of the moved files or folders; however, the
reverse is not true. Files or folders that are moved from an encrypted
NTFS folder to an unencrypted folder will not automatically be decrypted. Files must be explicitly decrypted.
Files
marked with the system files attribute and files residing in the system
root directory structure cannot be encrypted with EFS.
Marking
the encryption attribute of a file or folder does not prevent a user
with the appropriate NTFS permissions from deleting or listing files or
directories if their NTFS permissions allow those functions. Use EFS in
conjunction with NTFS permissions.
You
can encrypt or decrypt files and folders on a remote computer that has
been enabled for remote encryption. When you do, the data is transmitted
over the network in its decrypted form. Other protocols such as Secure
Sockets Layer (SSL) or Internet Protocol Security (IPsec) must be used
to encrypt the traffic.
As you would expect, you can
also implement EFS through the use of Group Policy. These settings are
located in Computer Configuration\Windows Settings\Security
Settings\Public Key Policies\Encrypting File System.
Through these settings, you
can choose whether you want to allow or deny the use of EFS for your
entire network. You can also choose to allow or deny the use of Elliptic
Curve Cryptography (ECC) encryption. ECC allows your network to be
complaint with Suite B encryption standards. Suite B standards meet the
Advanced Encryption Standard (AES) with key sizes of 128 and 256 bits
for symmetric encryption, Elliptical Curve Digital Signature Algorithm
(ECDSA) for digital signatures, Elliptic Curve Diffie-Hellman (ECDH) for
key agreement, and Secure Hash Algorithm (SHA-256 and SHA-384) for
message digest.
EFS is a great tool to help
you secure files and folders. As you implement an EFS program in your
network environment, you can provide access to files and folders while
maintaining very good security for those same files and folders.
But what about those system files?
2. Configure BitLocker Drive Encryption
In the previous section,
you learned that EFS will not provide encryption to any files marked
with the system attribute or files located in the system root directory.
So, what do you do with them? How do you secure the system files? The
answer is a tool called BitLocker. BitLocker was designed to encrypt the
partition on which the operating system files reside. Unlike EFS, which
allows the user to pick and choose files and folders for encryption,
BitLocker encrypts entire partitions or drives. BitLocker can be used to
encrypt the locally attached drives, while a tool called BitLocker To
Go can be used to encrypt devices such as USB sticks that may be
temporarily attached to the system. If a hacker were to attempt to get
at your system files, the files would be encrypted. If your drive were
stolen and put into another machine, the data would be inaccessible.
BitLocker makes use of a hardware module on the motherboard called a
Trusted Platform Module (TPM) chip. BitLocker uses it to seal the keys
that are used to unlock the encrypted operating system drive. When you
start your operating system, BitLocker requests the key from the TPM
chip and then uses it to unlock the drive.
When using a
BitLocker-encrypted drive, if you add new files to the drive, they are
automatically encrypted. Drives (fixed or removable) can be unlocked
with a password or a smart card, or you can set the drive to
automatically unlock when you log onto the computer.
BitLocker can be used in
conjunction with EFS. We recommend a strategy that maximizes the
security needs of your data, while minimizing the impact on the users
who will need access to that data.